本網站使用cookies以改善您的使用體驗,並提供更優質的客製化內容。若您未改變cookies設定並繼續瀏覽我們的網站(點擊隱私權政策以獲得更多資訊),或點擊繼續瀏覽按鈕,代表您同意我們的隱私權政策及cookies的使用。
Industrial
IEC 62443 工控安全

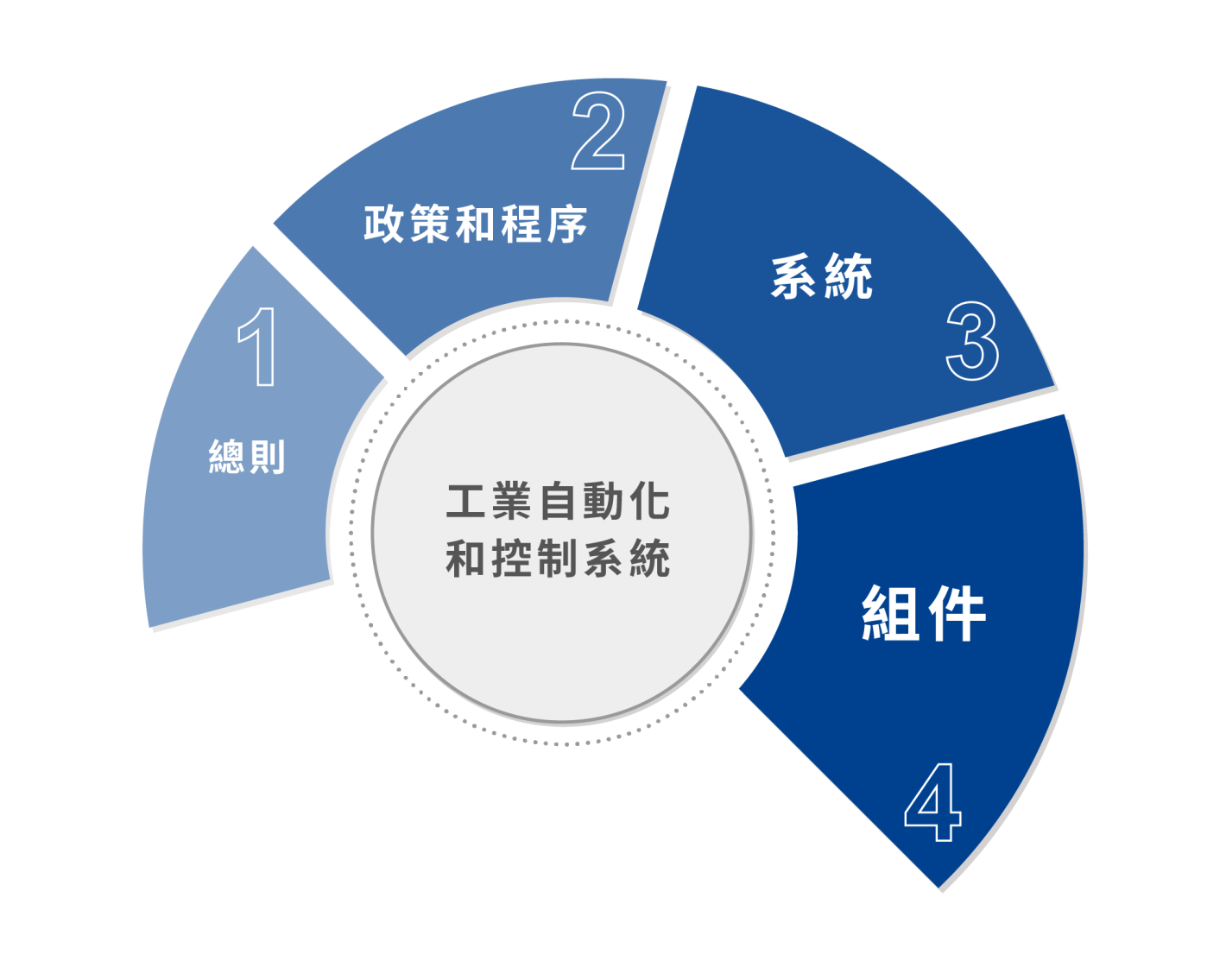
工控安全標準 IEC 62443
自2015 年 12 月 烏克蘭電力網路受到駭客攻擊,導致伊萬諾-弗蘭科夫斯克州大停電,這個世界第一起駭客攻擊造成電網大規模的停電事件,使關鍵基礎設施的資安威脅受到各方高度重視,而台灣從2018年的半導體業機臺中毒事件後,陸續發生了製造業、工業領域以及醫療產業的資安事件,而這些只是大規模複雜攻擊行動的一部分,上述這些網路罪犯攻擊重要基礎設施系統的案例,讓許多資安廠商紛紛針對重大民生基礎設施的資安風險與因應策略投入研究,而OT的資安也越來越受重視,也因此國際電工組織委員會自2013年開始陸續發布了IEC 62443的系列標準,而以製造業起家的台灣,自然而然也被歐美大廠要求需符合IEC 62443系列工控標準取得證書,以減少工控資安的風險。
Why ISA/IEC 62443
工業自動化及控制系統的安全(IACS)
- 一個系統設計時不夠安全,透過技術手段亦無法解決,需輔以適切管理及程序。
- 企業高度依賴IT科技,安全威脅無力抵抗,風險避無可避。
- 【人】永遠是資訊安全管理中最大問題。
- 攻擊技術日趨複雜,攻擊來源相當廣泛。
- 公用及私用網路互相連結分享資訊,增加存取控制的難度。
- 分散式電腦作業的趨勢削弱了集中式專責控管之效果。
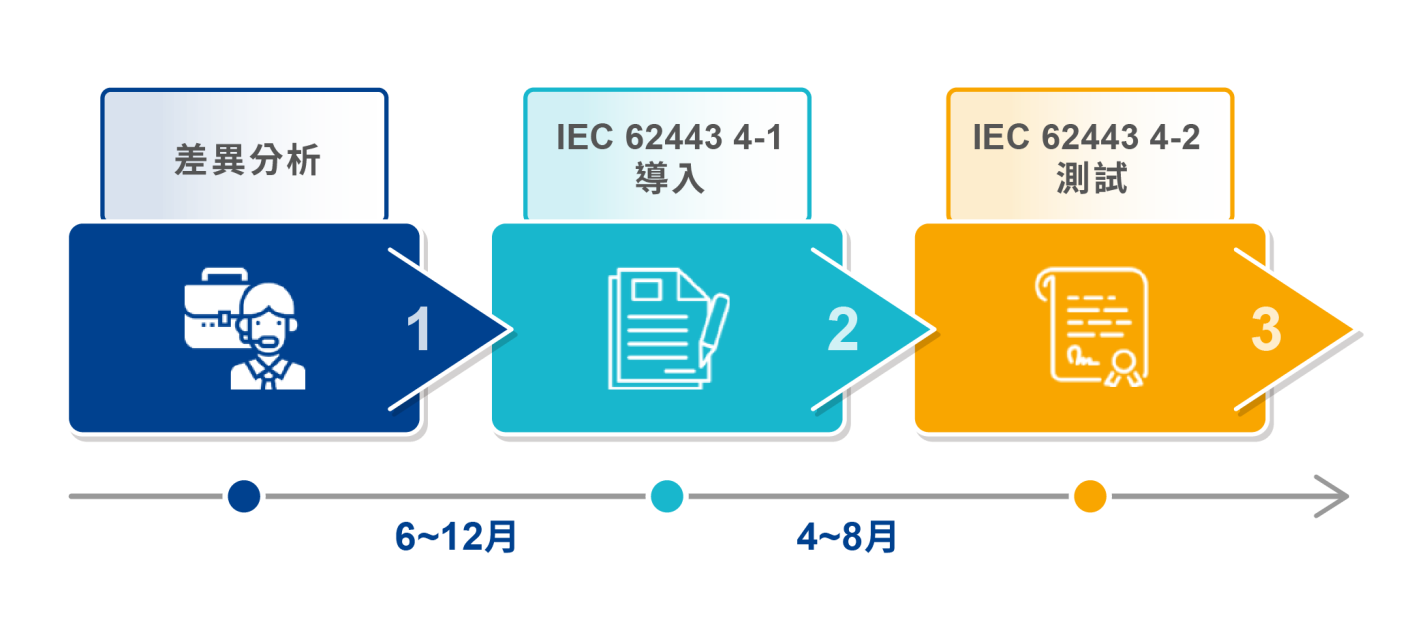
導入執行時程
- 資安作業可行性評估
- 產品資安測試(Pretest)
2. IEC 62443 4-1 導入
- 現況訪談
- 制訂組織與政策
- 規劃產品開發安全作業流程
3. IEC 62443 4-2 測試
- 資安檢測訓練
- 符合性測試
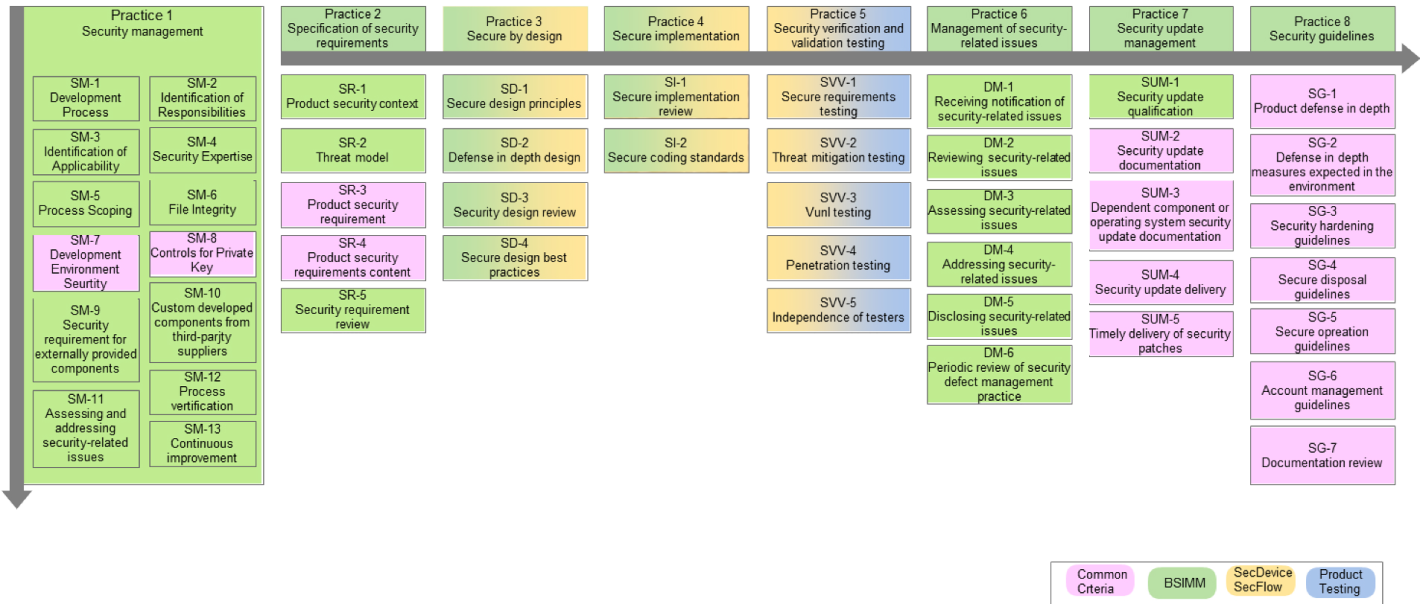
IEC 62443-4-1 產品開發要求
8 Practices, 47 Requirements
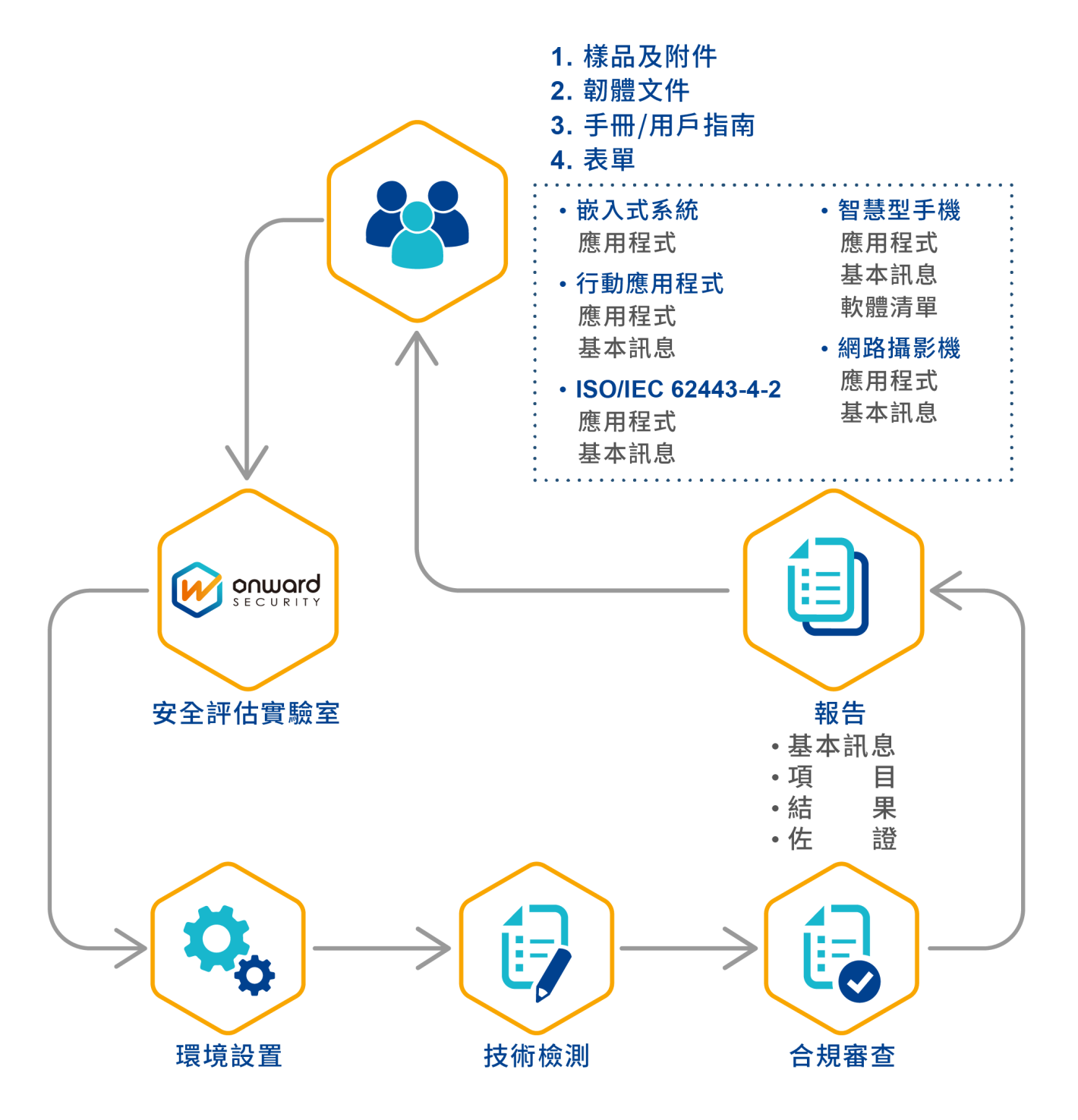
IEC 62443-4-2 工控系統(IACS)組件的技術安全要求
整合7項基本要求 95項安全要求
- IAC - 身份鑒別和認證控制
- RA - 資源可用性
- TRE - 實時事件響應
- RDF - 受限數據流
- DC - 數據機密性
- SI - 系統完整性
- UC - 用戶管控
組件要求 (CR)
- 軟體應用要求 (SAR)
- 嵌入式設備要求 (EDR)
- 主機設備要求 (HDR)
- 網路設備要求 (NDR)






