ICT
FIPS 140-3 for Cryptographic Modules

FIPS 140-3 Cryptographic Module Security Standard
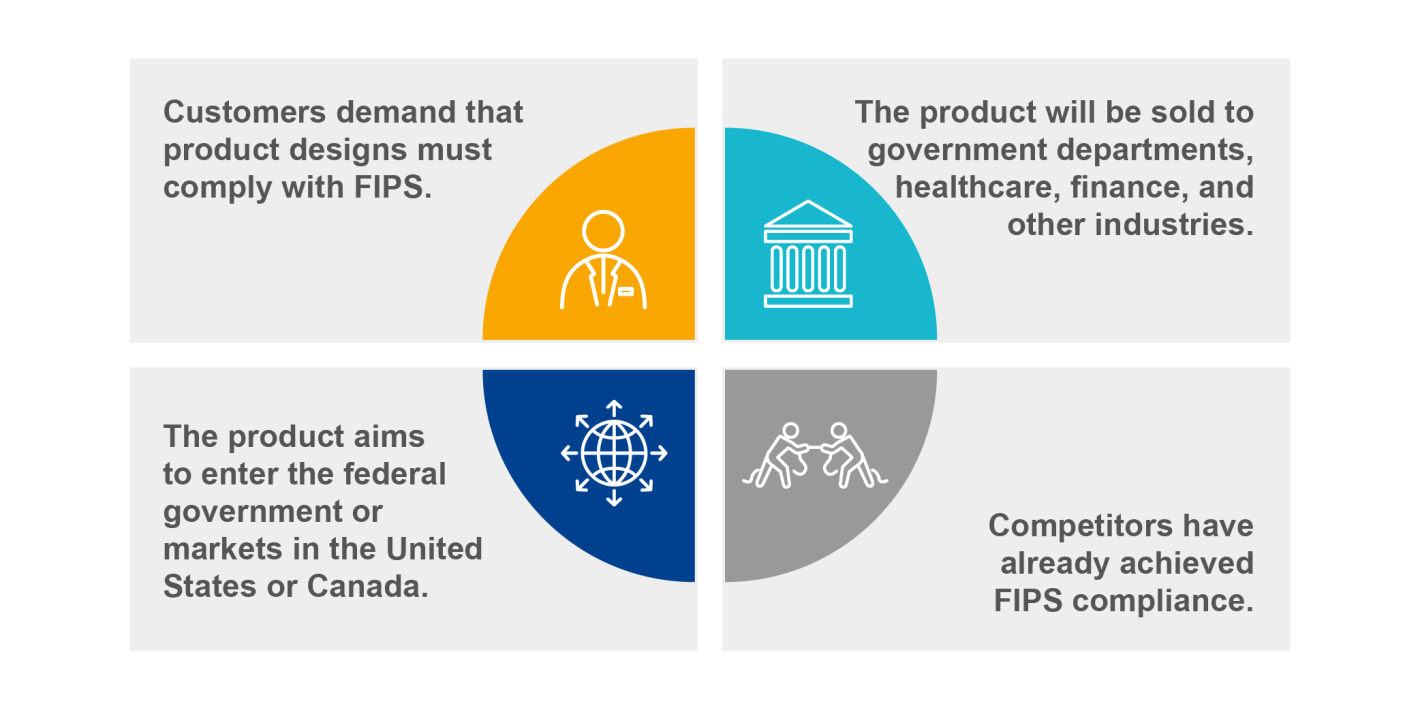
With the advancement of cryptographic technology, the FIPS 140 standard has evolved and is now updated to its third edition - FIPS 140-3. All cryptographic module developers, cryptographic accelerator developers, and other regulated industries selling any hardware or software cryptographic module must support the algorithms listed in the FIPS 140-3 approved list. Additionally, they must comply with the relevant algorithm and cryptographic module requirements and have these algorithms' actual operation validated by accredited laboratories. Due to the high security standards set by FIPS 140-3, industries such as healthcare and finance are evaluating and adopting this standard to protect their sensitive data, including personal data protection and cryptographic security.
Why FIPS?
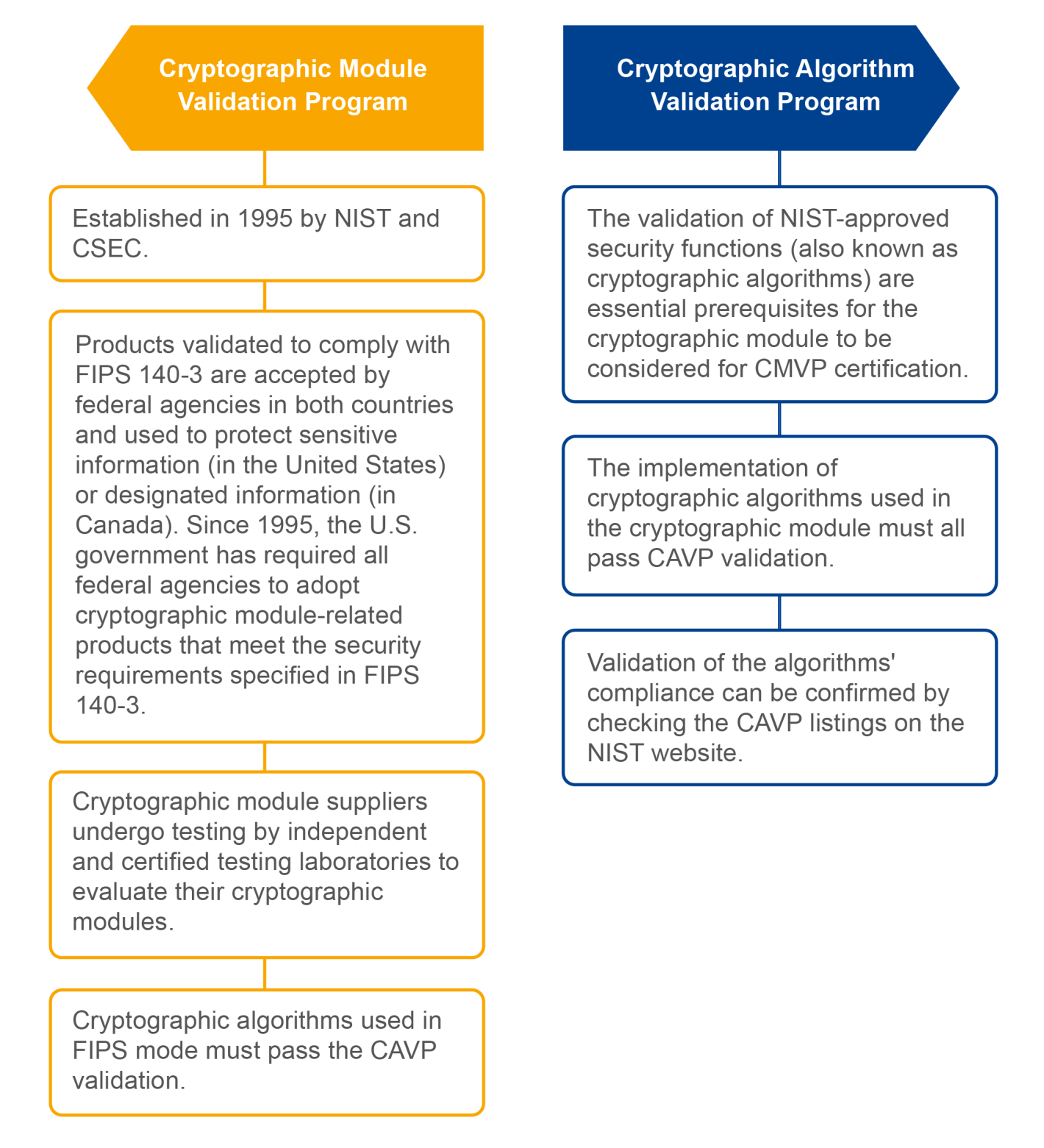
The FIPS 140-3 validation program and its related requirements include the following
The National Institute of Standards and Technology (NIST) of the United States has established cryptographic algorithm validation program and cryptographic module validation program as part of the FIPS 140 series standards. These programs provide testing and validation schemes for cryptographic algorithms and cryptographic modules, respectively:
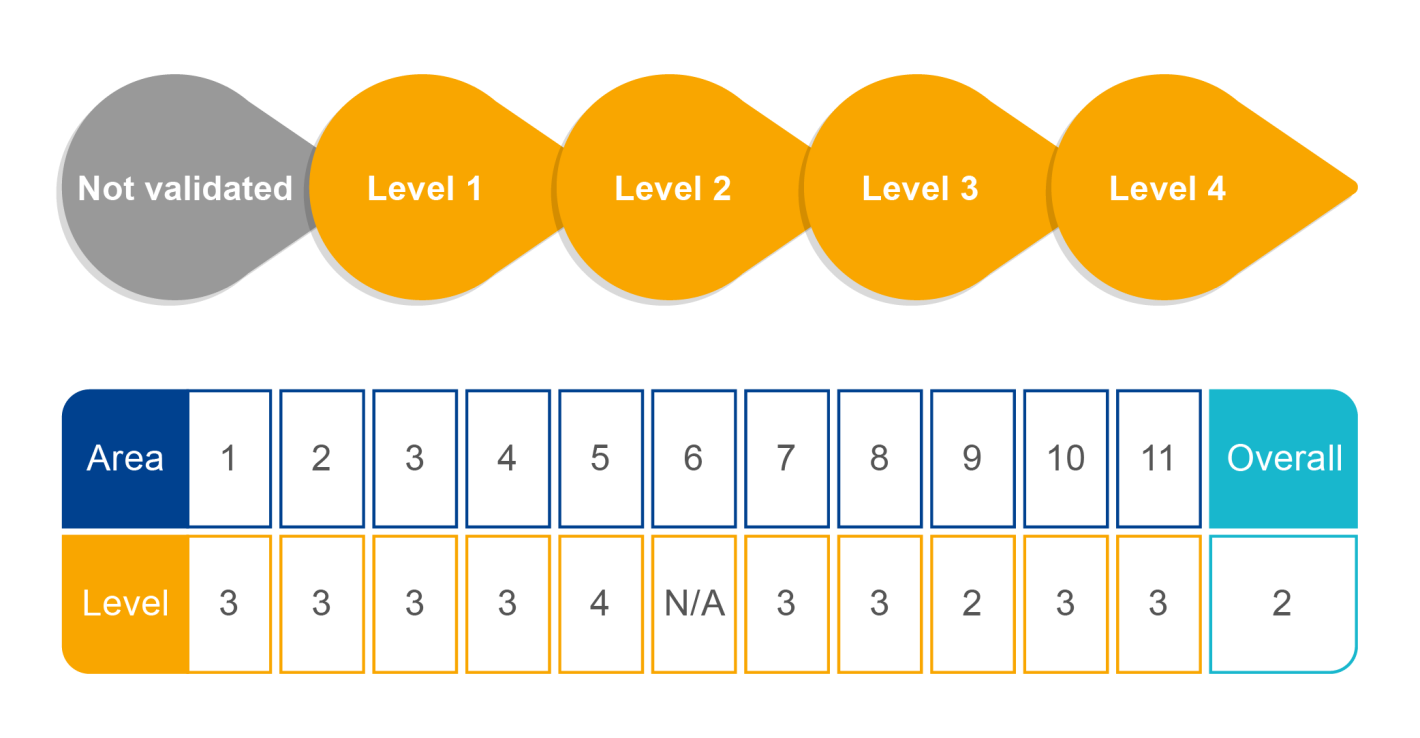
The four security levels of cryptographic modules (Security Level)
- Level 1 (Low) is the minimum requirement, and Level 4 (High) is the most stringent.
- Security requirements are cumulative, with higher levels encompassing all security requirements of lower levels.
- 11 security areas
- Each security area is rated between Level 1 to Level 4 security levels.
- The lowest security level rating among these determines the overall level of the cryptographic module (Overall Level).
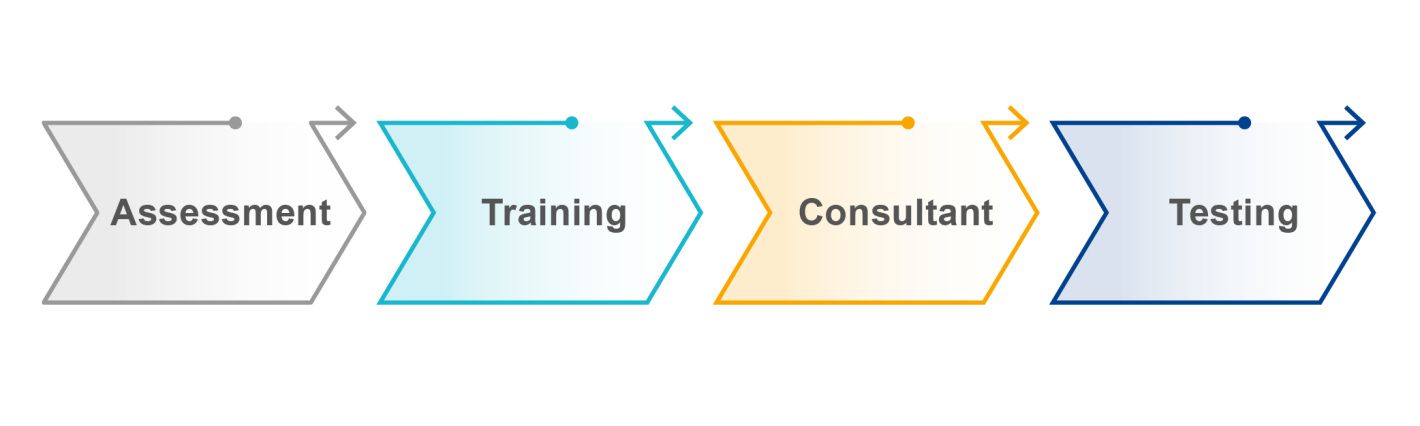
FIPS One-Stop Validation Service
Tailored validation solutions based on customer's industry characteristics and market demands
- No prior knowledge of FIPS is required; Onward Security can provide comprehensive FIPS education and training.
- We offer customized and complete validation plans to meet your specific needs and achieve optimal results.
- You are already a FIPS expert! Onward Security can provide the most down-to-earth and efficient testing and validation solutions.
Why Onward Security ?
- Compared to other foreign laboratories, Onward Security can provide assistance in Chinese to manufacturers, avoiding communication barriers that may delay acquisition of validation.
- When necessary, on-site guidance services can be provided, eliminating the delay of using online or written communication and enhancing the completeness and understanding of instructions.
- Concerns about time differences with foreign laboratories can lead to delayed communication and contact. Onward Security can offer customers the most timely and effective responses and solutions.






