Industrial
OT Security Standard IEC 62443

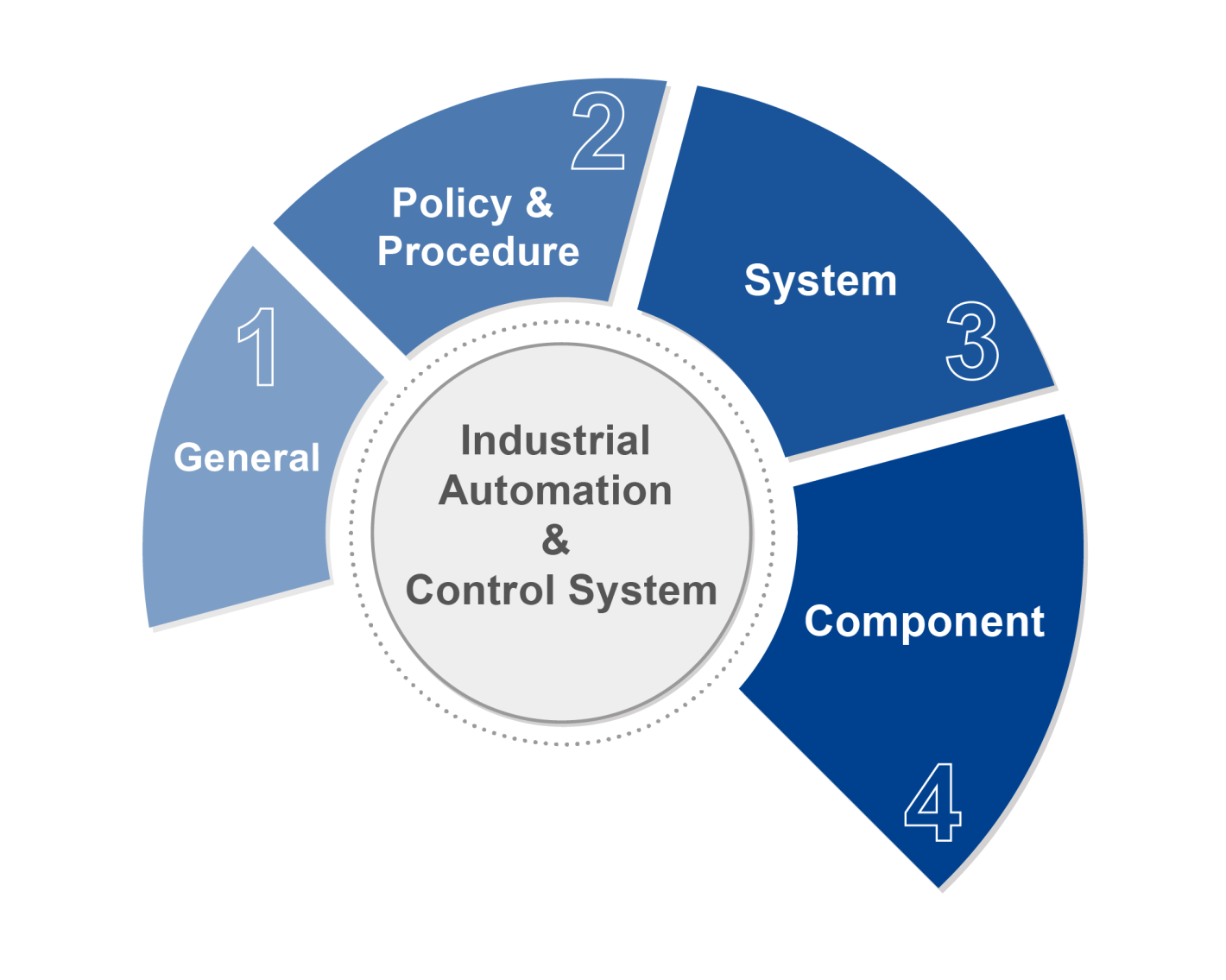
The Scope of IEC 62443 Standard
ISA/IEC 62443 has different series of standards. In addition to enabling upstream, midstream, and downstream manufacturers in various industrial control fields to have their own corresponding standards, when the standard is updated in the future, the certification only needs to be updated by certain organizations, instead of applying it to all manufacturers. For manufacturers, it can diversify information security risks, reduce the cost and manpower of implementing security standards, and can also be used when cybersecurity incidents occur, quickly find out the cause, and take appropriate measures.
Why ISA/IEC 62443
Cyber Security in Industrial Automation and Control (IACS)
- It the system design is not secure enough and can not be solved by technical means, then appropriate management and procedures are required.
- Enterprises highly rely on IT technologies. Consequently, they are not able to resist security threats and avoid risks.
- Human is always the biggest problem in cyber security management.
- The attack technologies are becoming more and more complex, and the attack sources are quite extensive.
- Public and private networks are interconnected to share information, making access control more difficult.
- The decentralized computer operation weakens the effect of centralized management.
Implementation Timeline
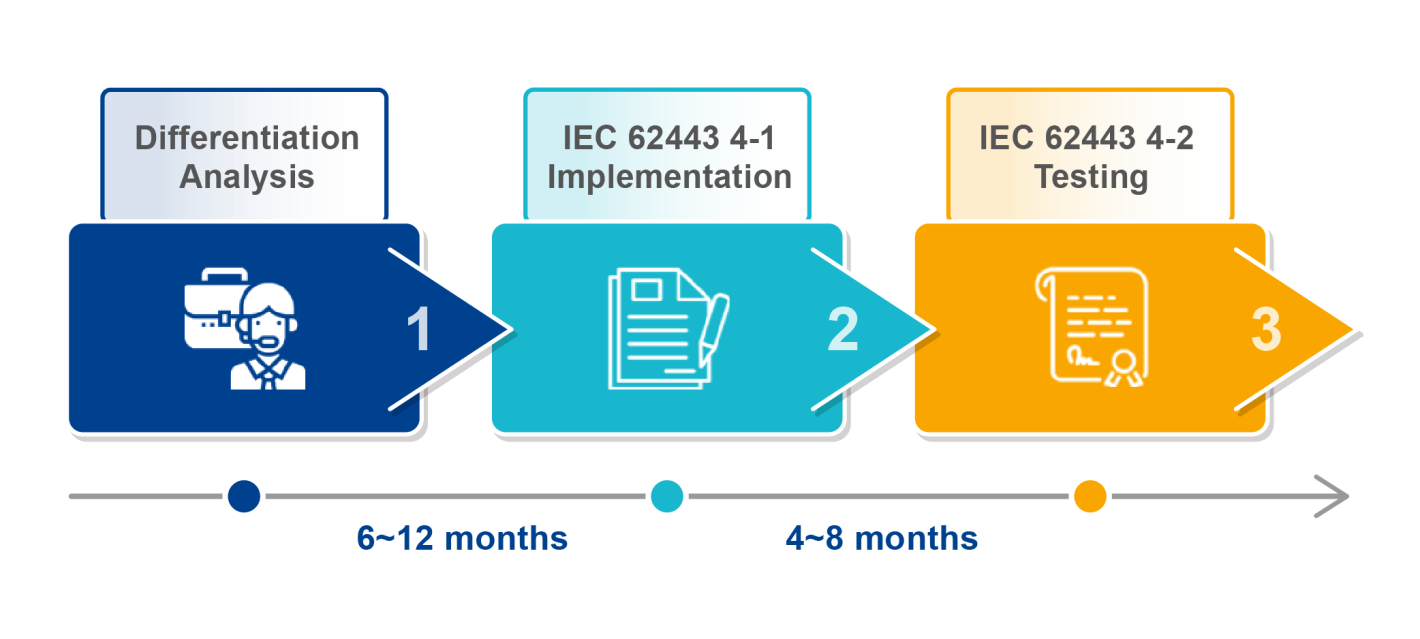
Security Development Service of Industrial Automation and Control (IACS)
The methodology of International Standard IEC 62443-4-1 is adopted to assist in the establishment of the secure product development plan
1. Differentiation Analysis
The methodology of International Standard IEC 62443-4-1 is adopted to assist in the establishment of the secure product development plan
1. Differentiation Analysis
- Feasibility evaluation of cyber security operation
- Product security test (Pretest)
2. IEC 62443 4-1 Implementation
- Status interview
- Organization establishment and policy formulation
- Plan security workflow of product development
3. IEC 62443 4-2 Testing
- Cyber security test training
- Compliance testing
IEC 62443-4-1 Product Development Requirements
8 Practices, 47 Requirements
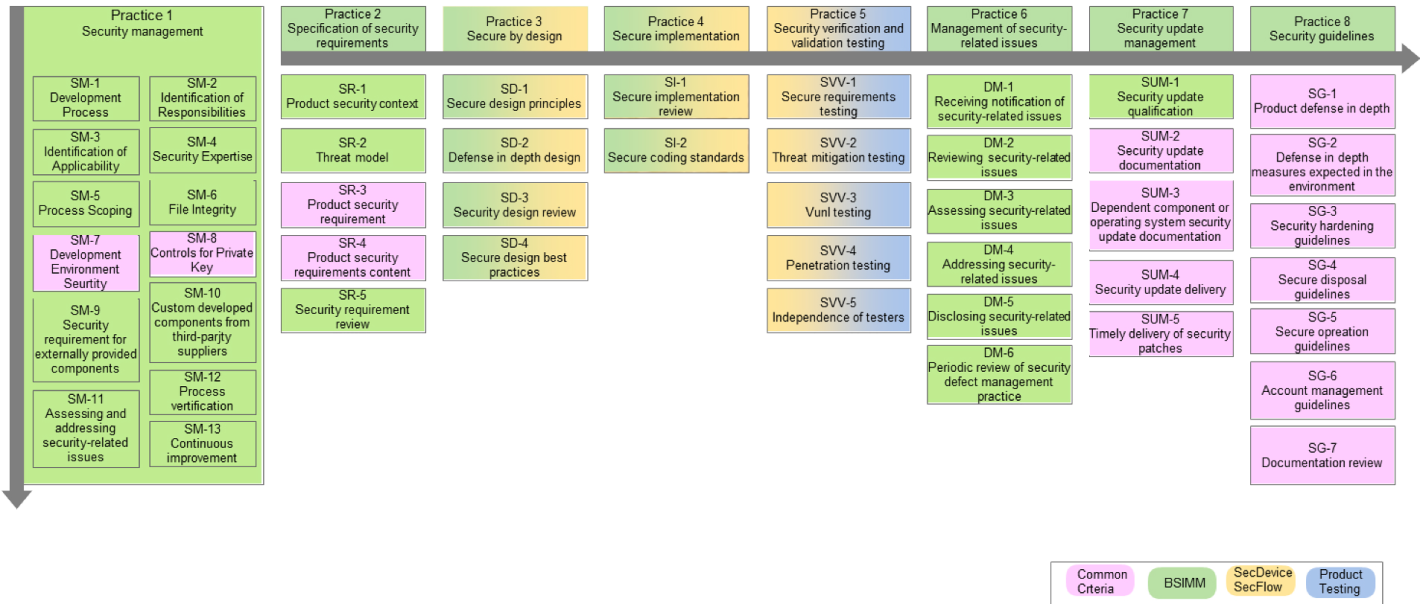
IEC 62443-4-2 Technical Security Requirements for IACS Components
7 Foundational Requirements. 95 Security Requirements
- IAC - Identification and Authentication Control
- RA - Resource Availability
- TRE - Timely Response to Event
- RDF - Restricted Data Flow
- DC - Data Confidentiality
- SI - System Integrity
- UC - User Control
Component Requirement (CR)
- Software Application Requirement (SAR)
- Embedded Device Requirement (EDR)
- Host Device Requirement (HDR)
- Network Device Requirement (NDR)






