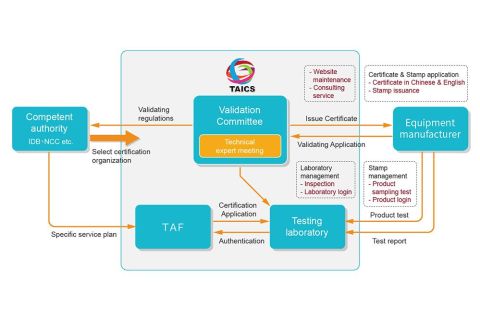
Blog
Building a More Resilient OT Security Framework with IEC 62443‑3‑2 & 3‑3
When OT systems are compromised, the impact extends beyond operations—it may threaten human safety. Recent cyber incidents targeting critical infrastructure sectors like manufacturing, energy, and transportation highlight that OT security must be a top priority.
Quantum Computing and Cybersecurity: A Threat Game Changer
Over the past decade, substantial investments in quantum computing have resulted in significant progress and increased awareness of its effect on cybersecurity.
EN 18031 Compliance: How Manufacturers Can Meet the EU RED-DA Cybersecurity Requirements
Discover how to meet EN 18031 cybersecurity requirements and avoid delays in EU market access under the new RED-DA regulation.
How to Effectively Manage ICT Supply Chain Security: Onward Security Reveals Critical Cybersecurity Strategies
The notorious SolarWinds attack in 2020 triggered global concern about supply chain security. SolarWinds, a key provider of network, systems, and IT infrastructure management solutions was widely used by 425 Fortune 500 companies at the time, underscoring its broad impact.
The Cost-Efficient, Time-Saving, and Multipurpose Certification: SESIP Emerges as the Hottest IoT Security Certification
In recent years, Internet of Things (IoT) devices have seen explosive growth, becoming essential for many organizational and personal applications.
Security Development in the Industrial Control Field! Myths and Key Concepts
With the rapid development of the Industrial Internet of Things (IIoT), modernized factories and production lines are increasingly depending on industrial control systems with Internet connections to maintain operations.
Why did the European Commission delay the application of the essential requirements for RED-DA?
As you may know the Radio Equipment Directive 2014/53/EU1 has established a regulatory framework for placing radio equipment on the single market. It mainly concerns mandatory market access conditions for radio equipment. The Delegated Regulation entered into force on the 1st of February 2022 and was supposed to become applicable from August 2024.
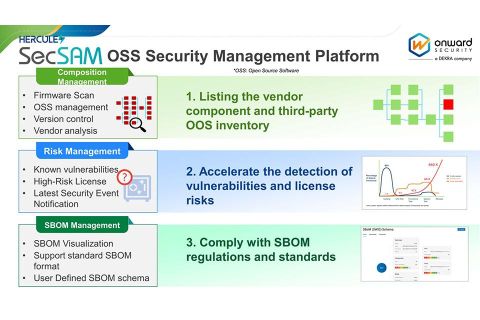
SecSAM: Empowering Your Supply Chain Management in Compliance with EO 14028
In light of Executive Order 14028 and the NTIA's publication of "The Minimum Elements for a Software Bill of Materials (SBOM)," this article highlights how SecSAM fulfills the requirements outlined in this executive order.
DEKRA launches the first Pilot Program for the Delegated Act of RED Directive
As the world becomes increasingly connected, Cyber Security is becoming more and more important. In order to ensure a safe and secure online environment, the European Commission has established a number of new regulations for Cyber Security as the NIS2 Directive, the Cyber Resilience Act, the Digital Operational Resilience Act, and the RED Delegated Act. Since security is firmly anchored in our DNA, DEKRA is actively participating in the development of these regulations.
How to comply with the mandatory cybersecurity regulation RED-DA in light of ETSI EN 303 645 standard becoming a global trend?
According to the upcoming EU Radio Equipment Directive: the Delegated Act for cyber security, RED-DA Article 3.3 d/e/f, which will be enforced in 2025, strict requirements are set for market entry of wireless devices, including consumer IoT products.
Cybersecurity Certification Program for Electric Vehicles Charging Stations
Electric vehicle (EV) charging stations can be targets for cyber-attacks. At DEKRA, we have designed the world’s first cybersecurity certification program to evaluate and demonstrate the security of EV charging stations.
From Penetration Testing to Red Team Assessment, the Diagnosis of Potential Information Security Threats is Expanded
More companies tend to adopt penetration testing. Through annual penetration testing, they plan to identify potential security vulnerabilities in key systems and fix them accordingly.
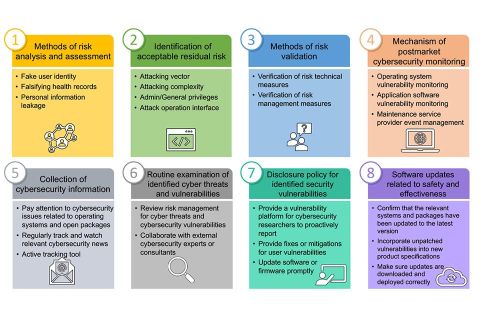
An Imminent Task in 2023: How to Protect OT Systems with IEC 62443-2-4 & 3-3
With the proactive engagement by the manufacturing sector in digital transformation, the line between operational technology and information technology has been blurring in recent years.
Smart medical cybersecurity legislation promulgated - How should medical device manufacturers deploy?
In recent years, the epidemic has acted as a catalyst to accelerate the digital transformation of many fields, and smart medical care is one example. However, it cannot be denied that digital transformation is like a double-edged sword. It benefits the country and the people, but it also expands the scope of cyber attacks, allowing hackers to take advantage. In view of this, a number of regulations have been released one after another, such as the US FDA, EU MDR/MDCG, etc.
How can connected cars resist malicious attacks ? - The latest security trends in the automotive supply chain
The Internet of Vehicles (IoV) has transformed the automotive industry. All kinds of connected cars have sprung up, such as vehicles equipped with Advanced Driver Assistance Systems (ADAS), self-driving cars, and electric vehicles. These vehicles improve mobility and convenience but also face cyber attacks. The number of malicious attacks on connected cars has increased from about 65 million in 2011 to about 1.1 billion in 2020. With more than 11,000 Common Vulnerabilities and Exposures (CVEs) released worldwide, attacking connected cars has become a new target for hackers.
ioXt intelligence: A Q&A with Morgan Hung, general manager of Onward Security
From cybersecurity certifying top global manufacturers and brands like TikTok to partnering with government agencies like National Institute of Standards and Technology (NIST), ioXt Alliance is fortunate to collaborate with leaders and influencers involved in the IoT industry. And, we want to bring you their thoughts on the topics that matter most.
Eliminate FinTech cybersecurity risks with APP and SWIFT CSP compliance
As the world has continued to be shrouded in the pandemic in recent years, it has accelerated the progress of digitalization and also injected a catalyst for FinTech (financial technology). However, it seems to be a double-edged sword, leading to more frequent hacking attacks and making cybersecurity a hot topic in the financial industry.
The pandemic accelerates the cybersecurity of smart medical devices, the 8 key points of cybersecurity risk assessment
With the rise of wearable devices, IoT devices such as smart bracelets have gradually become the best choice for personal health care through network applications. Since 2020, governments around the world have faced a shortage of medical resources when actively confronting COVID-19 pandemic prevention. It has prompted governments to start planning how to effectively use the popularity and convenience of the Internet to develop smart medical policies and increase telemedicine services in the current severe pandemic or post-pandemic era, so as to avoid the collapse of the medical system caused by the recurrence of the pandemic.
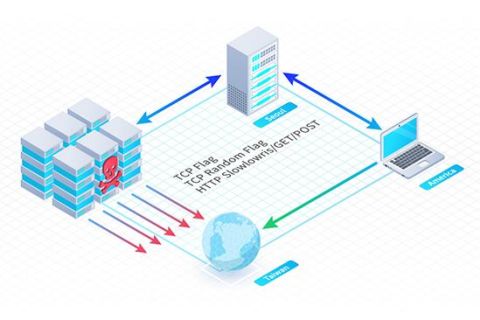
DDoS attack re-evolution: TCP Middlebox Reflection can amplify packets by 65-fold
Researchers have observed multiple Distributed Denial-of-Service (DDoS) attacks in recent weeks. These attacks include high-traffic attacks such as SYN flood, and have caused high amounts of traffic that peaked at 11 Gbps. After analyzing the packets used in these DDoS attacks, researchers discovered that the hackers were using a new technique called TCP Middlebox Reflection. It is a very new attack method, first disclosed in a paper by researchers at the University of Maryland and the University of Colorado Boulder in August 2021.
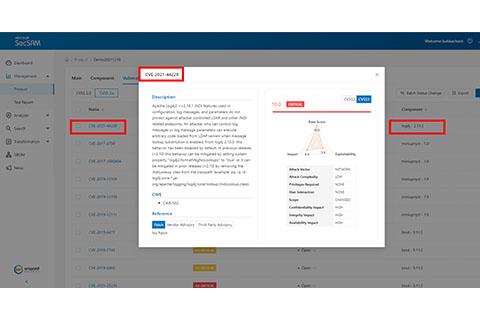
Avoid falling victim to the worst zero-day vulnerability in recent years! Understanding what Apache log4j is? How to patch the CVE-2021-44228 vulnerability
The Apache Foundation issued a serious vulnerability warning about log4j earlier. Log4j is a common open-source logging framework. Many developers use it to log activity in their applications. The reported remote code execution vulnerability (CVE-2021-44228) exists in all versions of log4j 2.x to 2.16.0 (released 2021/12/13). This vulnerability is called "Log4Shell".
Cyber terrorists rock multi-billion-dollar industry, and the baby’s crib
The plethora of security risks that sit at the nexus of artificial intelligence (AI) and the connected technologies that keep a watchful eye on our little darlings raise grave concerns for cybersecurity leaders and parents alike – rightfully so given our increasing reliance on them.
Are CISOs fuzzing with IoT? We hope so.
Were we privy to the nefarious actor’s playbook, we would see that intruders and insider threats alike share a motif deeper than the enterprise’s bottom line — to compromise its unknown vulnerabilities — and they’re targeting the plethora of security risks in the Internet of Things (IoT) technology to get there.
Software vulnerabilities become hacker targets again - How to address supply chain security risks?
The source of this risk affecting dozens of brands and millions of devices is a path traversal vulnerability. The Path Traversal vulnerability allows hackers to bypass authentication and browse numerous directories on the victim host. Once hacked, hackers can gain control of the victim host, and even gain superuser (also called root) privileges. Because of this, the CVSS v3 score for the CVE-2021-20090 vulnerability is as high as 9.8.
Cyber power systems strengthens the cybersecurity confidence of its PowerPanel Cloud service through CREST penetration test
In order to prove that it has reached a certain level of cybersecurity, Cyber Power Systems has set high-standard testing requirements. Referring to the list of qualified vendors for penetration testing announced by the world-renowned CREST organization, the company entrusted Onward Security, the only recognized company in Taiwan, to conduct a complete inspection of PowerPanel Cloud in accordance with international standards.
Security leaders scale cyber strategies to rival 5G threatscape
Fifth-generation mobile networks (aka 5G) have morphed into an evolving international battleground for foreign adversaries and cybersecurity leaders, but Daniel Liu, CTO at Onward Security, forecasts a promising security posture as organizations around the world ramp up their cyber strategies.
Industrial automation and control systems under cyberattack
From Germany’s steel mill, Ukraine’s power grid, Saudi Arabia’s oil and gas facility, to electric utilities and critical infrastructure worldwide — adversaries are game for everything and they’re perfectly capable of wrecking industrial automation and control systems (IACS).
Vulnerabilities are impacting millions of smart and industrial IoT devices
The multi-billion-dollar Internet of Things (IoT) market has manufacturers pining for a competitive edge and their risky shortcuts to lead the race have security leaders on high alert.
Cubo Ai smart baby monitor received the US CTIA certification to make parents feel more at ease
Since the monitors were launched in the market, they are showing excellent results in Taiwan and English-speaking countries, especially in Australia, which is even the best-selling product among their competitors. "Although the R&D team of the company has already added the consideration of cyber-security during the design stage, and is confident in having the capability of minimizing the risk of the monitor being hacked", said Steven Shen. However, from time to time, Cubo Ai has received users’ concerns about cyber-security and they are deeply afraid of the risk of privacy leakage or even the risk of babies being frightened by the monitor.
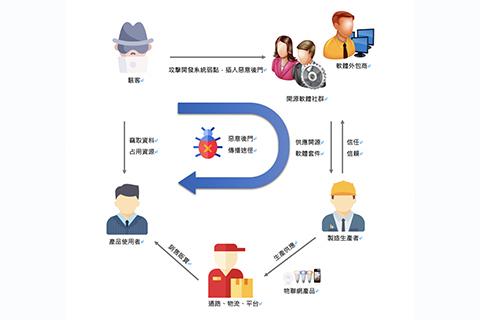
Hackers using open-source software to attack supply chains nowadays, open-source software becomes the scapegoat
Hackers are continuously growing their cyberattack methods in various ways. The Advanced Persistent Threat (APT) is moving their target from enterprises’ cybersecurity to the supply chain. The cybersecurity team constantly ignores open-source software security issues. Therefore, it wins hackers' favor.
Rapid development of 5G applications prompts urgent need for devices to obtain IoT cybersecurity certification
Connected devices for a diversity of applications are burgeoning thanks to widespread availability of 4G communication. As these connected devices are everywhere in our daily lives, any product security vulnerability could result in data breach and comprise user privacy. With governments and leading enterprises around the globe stepping up cybersecurity efforts, manufacturers have begun to engage third-party cybersecurity test labs to help validate their security implementations.
World-renowned IoT equipment vendor uses HERCULES SecFlow and HERCULES SecDevice to implement SSDLC
In the frequent attacks on IoT devices, the vulnerabilities that Company A faces include that malicious attacks are triggered by improper handling of device firmware credentials; account secrets with weak encryption storage methods allow hackers to hack into devices; device vulnerabilities can be used by hackers as a springboard for attack paths and the severe cases can lead to the risk of consumer privacy leakage. All these issues have aroused the concern of consumers and government agencies.
U.S. Federal Information Processing Standard 140-3 Outlines Cryptographic Modules to Prevent Sensitive Data Leak
In the future, all the hardware or software cryptographic modules provided by regulated industries such as cryptographic module vendors and cryptographic accelerator vendors, shall support the algorithms in the FIPS 140-3 certification list, which must also comply with relevant algorithms and cryptographic module requirements.
Cybersecurity defense practices for smart factory (Part 2)
Due to the characteristics of industrial production, there are bound to be risks in the production process. From the input of raw materials and various cutting and grinding that produce physical and chemical changes during the automated process, to the output of products and the disposal of remaining waste, negligence of cybersecurity in any link may affect the manufacturing process and cause significant losses.
Critical vulnerabilities expected to ripple through the IoT landscape
CISOs will tell you that weaving security controls into product development is a daunting challenge and failing to do so has detrimental consequences.
Cybersecurity implementation and certification becoming the essentialities for IoT equipment
With the increasing attacks on IoT devices, more and more IoT equipment are applied to different industries, the IoT security issue has attracted attention. Therefore, the cybersecurity standard implementation for IoT equipment has become crucial in recent years.
Challenges and solutions of global equipment manufacturers on DoS attacks
The diversified development of the Internet of Things (IoT) has brought business opportunities to various sectors. Many industries have successively launched connected products. In addition to the smart home appliance, smart camera and other consumer products, the non-consumer equipments in industrial control, medical, communications, transportation and other industries have also joined the ranks of the IoT. However, for this booming business opportunity, no one is happiest than the black industry chain. The fields that were originally difficult to capture have created new blueprints for attacks because of devices connected to the Internet. Instantly, devices newly added to the connected world become targets for hackers to access.
Industrial control security standard and practice - A brief overview of the IEC62443
On December 23, 2015, the Ukrainian power grid was attacked by a hacker, resulting in a blackout in the Ivano-Frankivsk region. This is the world’s first large-scale power outage caused by a hacker attack, and has caused all parties to attach great importance to the cybersecurity threats of critical infrastructure.
Minimizing threat risk with establishing industrial control cybersecurity process and obtaining international verification
In the past few months, there have been many major domestic cybersecurity incidents . During May, the large petrochemical company and the semiconductor assembly and test factory were infected with ransomware. During June, the automation equipment factory was infected with ransomware, and the PCB manufacturer was infected with viruses. In July, the major wearable device manufacturer was also attacked with ransomware. At the same time, more and more malicious programs designed for industrial control equipment have been exposed, such as EKANS (Snake) targets GE's Historian, LogicLocker targets PLC, and Triton targets Schneider's TriconexSIS controller.
Cybersecurity defense practices for smart factory (Part 1)
In recent years, the government has been vigorously promoting Industry 4.0, also known as Smart Factory. Its focus is on the intelligence of the production line, which needs to integrate existing IT and OT technologies, and use numerous IoT devices, so as to meet the rapidly changing needs of customized manufacturing. In order to optimize the production process, it is an inevitable trend to adopt and deploy a large number of cybersecurity equipments.
Mobile APPs are booming, but are the APPs you use really safe?
With the development of technology and network transmission, mobile applications are increasingly popular. Many APPs have sprung up to bring people a high degree of convenience. Eating, clothing, housing, transportation, education and entertainment can be done through APPs.
The solution to known vulnerabilities in open source package - take the SSL vulnerability as an example
Remember that? In April 2014, the open-source OpenSSL Management Committee issued a serious information security vulnerability that shocked the world. A vulnerability called Heartbleed allows attackers to read server memory. In that year, it affected more than half of the world's website operations. However, as time progresses, it is not difficult to find that this is not the only vulnerability caused by Secure Sockets Layer (SSL). What other potential threats from the SSL vulnerabilities can lead to risks? How to effectively detect and prevent threats early? This article will help you understand more about them.
Introduce the latest IoT device certification processes to deal with the frequent information security attacks
Whenever emerging technologies and applications appear in the market, problems sometimes arise that were not thought of when they were originally planned. This is just like the launch of Internet of Things (IoT) products. They are accompanied by some security attacks such as the Mirai Botnet in 2016 [1]. When we discuss the security attacks on the IoT products, we often find that the attacks are because users have not changed the default password of the IoT product login page. Moreover, users do not fully understand and are unfamiliar with the functions provided by IoT products, so that these products with remote login functions are exposed on the Internet.
Onward Security provides Asia's first Amazon, CTIA, ETSI EN 303 645 security assessment services
With the world going digital, the popularity of Internet of Things (IoT) devices is rapidly rising. This is not only reshaping people's lives but also spurring a wave of new market opportunities. However, growingly widespread use of connected devices also leads to increased cybersecurity threats. To control cybersecurity risks, governments around the world are enacting cybersecurity laws while leading manufacturers are also implementing cybersecurity requirements for their products.
Onward Security Connected Devices Secured
In the IoT era, device manufacturers are strongly promoting network-enabled products while trying their best to shorten their time-to-market. In their effort to speed up product development, few blind spots in data protection indomitably arrive.
How to balance the agility and security of product development? About the complementarity of DevSecOps and automation
The importance of DevSecOps can be learned from the past. In 2019, a tragic case was that Facebook once again faced the data leak. More than 267 million Facebook user profiles were exposed on the online database of the Dark Web, including names, IDs and phone numbers. These users may be subject to cyber attacks of spam or phishing emails, which caused Facebook to suffer a loss of credit and a stock price crash.
The stay-at-home economy thrives during the pandemic, how to stop hackers and protect online transactions
Starting from February 2020, the COVID-19 pandemic has created a whirlwind of stay-at-home economy in the market. The usage rate of e-commerce platforms and video streaming platforms has increased significantly. However, many information security issues are hidden in online trading websites or platforms. As early as 2016, a security researcher had notified Uber of a security vulnerability that could allow attackers to brute force guessing to obtain Uber coupon codes with limited usage and value in the US dollar between $5,000 to $25,000[6].
Intelligent manufacturing faces security challenges and opportunities in the coming IIoT era
With the advancement of artificial intelligence (AI) technology, intelligentization has become the main theme of technology development in the 21st century. The core technology of intelligent manufacturing is the Internet of Things (IoT) technology and the Cyber-Physical System (CPS). By combining big data analysis, artificial intelligence, cloud computing and other technologies, intelligent manufacturing is trying to intelligentize every step of the production process, thereby achieve the customized business goal to meet the small and diverse market demand.
How the diversified IoT devices comply with cybersecurity regulations
Coming to 2020, the development of Artificial intelligence (AI) and 5G is still in full swing. At the same time that 5G is entering the commercial phase, the development of Internet of Things (IoT) with the strength of the hardware industry has also become more vigorous. With the popularity of IoT, the cybersecurity threats of edge devices have increased.
Onward Security enables enterprises to win IoT business opportunities
Driven by the advancement of semiconductor manufacturing process and the increasingly robust cloud service, the adoption of Internet of Things (IoT) devices is growing steadily. What follows is that many security incidents that caused significant losses occurred due to insufficient product security, such as the Mirai Botnet that occurred in 2016.
Onward Security promotes DevSecOps to address challenges in cybersecurity regulatory compliance
In the IoT era, device manufacturers or brands are strongly promoting network-enabled products while trying their best to shorten time-to-market. In their effort to speed up product development, they may overlook some blind spots in data protection and put devices with security vulnerabilities on the market. More often than not, such security vulnerabilities are discovered by foreign government agencies or hackers, which may not only cause harm to consumer privacy but also lead to litigations that damage to business reputation and brand image.