Software Supply Chain Security
26.Jul.2023
SecSAM: Empowering Your Supply Chain Management in Compliance with EO 14028
In light of Executive Order 14028 and the NTIA's publication of "The Minimum Elements for a Software Bill of Materials (SBOM)," this article highlights how SecSAM fulfills the requirements outlined in this executive order.
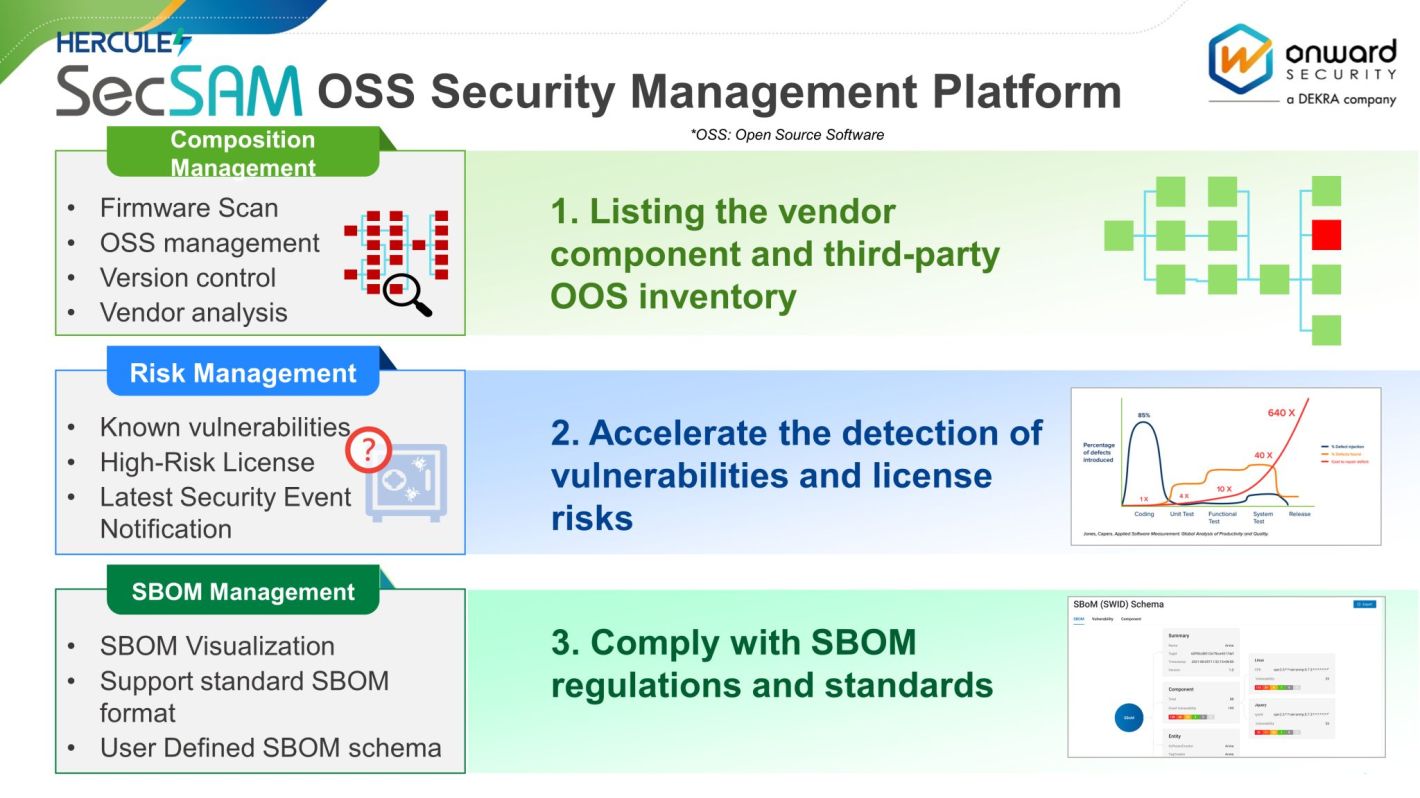
EO 14028 demands that SBOMs adhere to SPDX, CycloneDX, and SWID formats and track their dependencies across different versions. SecSAM goes beyond being a mere SBOM generator; it boasts powerful component management capabilities that assist users in monitoring component applications across various versions, facilitating efficient component relationship management. Moreover, SecSAM supports standard format SBOM outputs, including SPDX and SWID (2023 Q4 release). With increasing support for multiple formats, seamless conversion between different formats becomes possible, eliminating concerns about integrating SBOMs submitted by various suppliers.
As an advanced component management system, SecSAM boasts automated continuous monitoring of Open Source Software (OSS). The platform synchronizes vulnerability information from NVD daily, promptly notifying users of any newly discovered weaknesses in the utilized OSS components. When generating SBOMs using SecSAM's automated tools, the system also provides valuable License information and past litigation cases associated with OSS components, alleviating any uncertainties regarding OSS licensing for customers.
In line with the spirit of EO 14028, the focus is not solely on SBOM generation and management; supplier component management is equally vital. For organizations, managing components across different suppliers can be challenging. However, SecSAM offers a solution by enabling the creation of sub-accounts for various suppliers, allowing them to manage their components independently. Suppliers cannot access each other's account information, but the organization gains visibility into all the information. With daily vulnerability updates, suppliers and the organization's personnel can receive synchronized component vulnerability monitoring information, significantly reducing communication costs. SecSAM is your company's ultimate companion for robust supply chain management.
In conclusion, SecSAM meets the SBOM requirements specified in EO 14028, offers advanced component management capabilities, and facilitates efficient supplier collaboration. As your organization strives for enhanced cybersecurity and streamlined supply chain management, SecSAM is the ideal solution to fortify your cybersecurity posture and embrace the principles outlined in EO 14028. Elevate your cybersecurity game with SecSAM today!
EO 14028 demands that SBOMs adhere to SPDX, CycloneDX, and SWID formats and track their dependencies across different versions. SecSAM goes beyond being a mere SBOM generator; it boasts powerful component management capabilities that assist users in monitoring component applications across various versions, facilitating efficient component relationship management. Moreover, SecSAM supports standard format SBOM outputs, including SPDX and SWID (2023 Q4 release). With increasing support for multiple formats, seamless conversion between different formats becomes possible, eliminating concerns about integrating SBOMs submitted by various suppliers.
As an advanced component management system, SecSAM boasts automated continuous monitoring of Open Source Software (OSS). The platform synchronizes vulnerability information from NVD daily, promptly notifying users of any newly discovered weaknesses in the utilized OSS components. When generating SBOMs using SecSAM's automated tools, the system also provides valuable License information and past litigation cases associated with OSS components, alleviating any uncertainties regarding OSS licensing for customers.
In line with the spirit of EO 14028, the focus is not solely on SBOM generation and management; supplier component management is equally vital. For organizations, managing components across different suppliers can be challenging. However, SecSAM offers a solution by enabling the creation of sub-accounts for various suppliers, allowing them to manage their components independently. Suppliers cannot access each other's account information, but the organization gains visibility into all the information. With daily vulnerability updates, suppliers and the organization's personnel can receive synchronized component vulnerability monitoring information, significantly reducing communication costs. SecSAM is your company's ultimate companion for robust supply chain management.
In conclusion, SecSAM meets the SBOM requirements specified in EO 14028, offers advanced component management capabilities, and facilitates efficient supplier collaboration. As your organization strives for enhanced cybersecurity and streamlined supply chain management, SecSAM is the ideal solution to fortify your cybersecurity posture and embrace the principles outlined in EO 14028. Elevate your cybersecurity game with SecSAM today!