Security Incident
11.Jan.2021
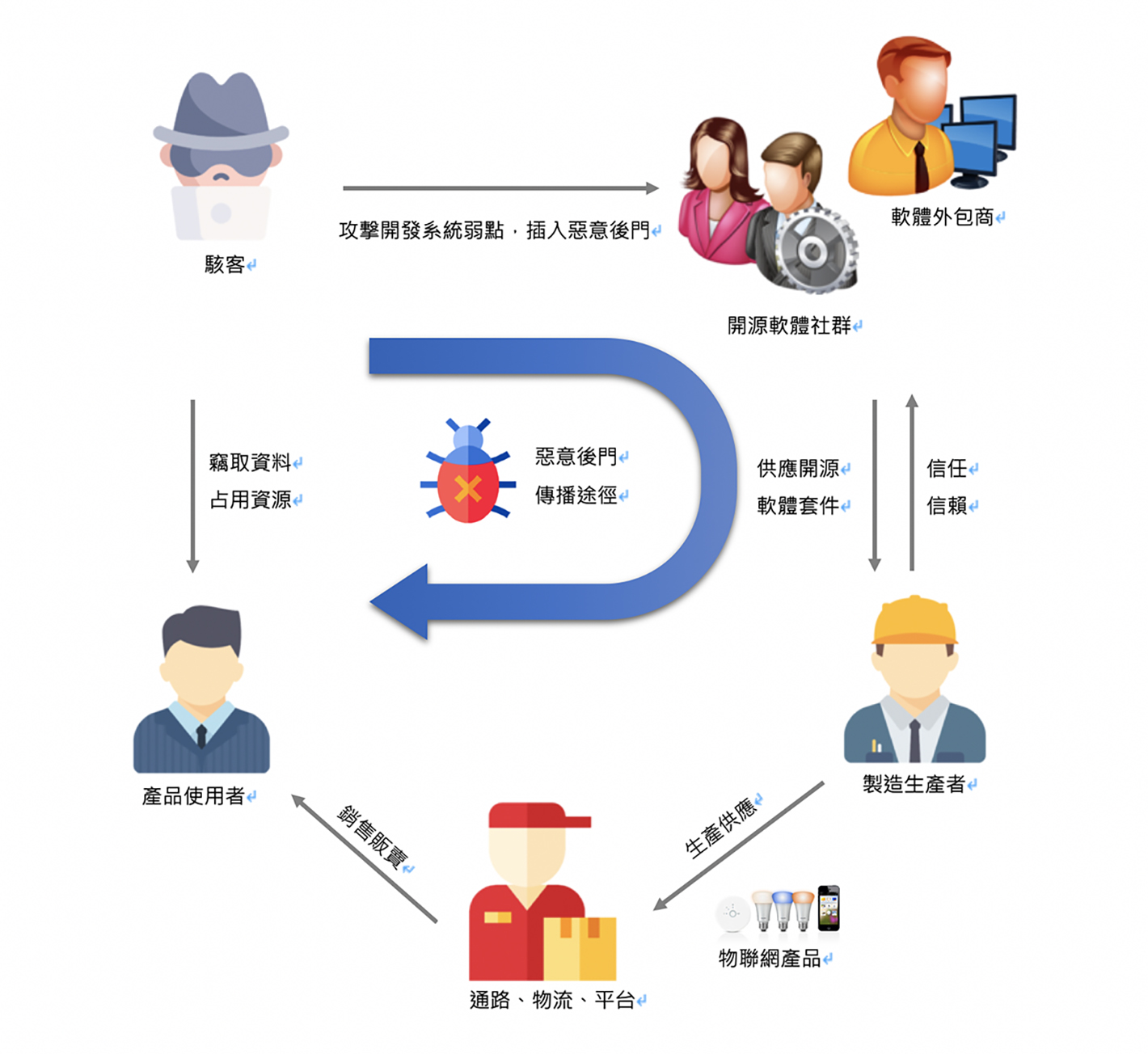
Hackers using open-source software to attack supply chains nowadays, open-source software becomes the scapegoat
Hackers are continuously growing their cyberattack methods in various ways. The Advanced Persistent Threat (APT) is moving their target from enterprises’ cybersecurity to the supply chain. The cybersecurity team constantly ignores open-source software security issues. Therefore, it wins hackers' favor. The well-known provider of internet hosting for software development, GitHub, was hacked by hackers implanting malware in their source code. This attack was letting all developers who were using open-source code become helpers in creating backdoor programs for hackers unintentionally. When these back doors’ products are launched, they will be distributed on home networks, corporate networks, critical infrastructure, and so on. It will directly allow hackers to expand on the attacking area. On the manufacturer side, there will be a lot of following repairing work, also cost and reputation lost.
In fact, the above situation can be avoided as long as people improve their cyber-security knowledge which is putting cyber-security awareness into the development process before the product is launched. There is one cost-effective way, by using automated tools to identify the weaknesses of third-party open-source code during development, manage and repair the discovered weaknesses. As a result, it can successfully avoid becoming a security breach in the supply chain and reduce weaknesses from being exploited.
In fact, the above situation can be avoided as long as people improve their cyber-security knowledge which is putting cyber-security awareness into the development process before the product is launched. There is one cost-effective way, by using automated tools to identify the weaknesses of third-party open-source code during development, manage and repair the discovered weaknesses. As a result, it can successfully avoid becoming a security breach in the supply chain and reduce weaknesses from being exploited.
Onward Security Solutions
"HERCULES SecFlow - Product Security Management System" allows the R&D team to check whether there are major cybersecurity vulnerabilities in the system through using Open Source Risk Management during the software design and development stage, thereby protecting and correcting from the source;"HERCULES SecDevice - Automatic Vulnerability Assessment Tool" provides networking product testing environment configuration, security assessments, and other automated functions. More than 140 test items are provided in this system, it is able to assist to find out the known and unknown weaknesses in the development process of IoT products, to further correct the mistakes at the source.
Compliance & Certification Services: It can improve the common product development life cycle management problems of enterprises. Customizing the product Security Management process, providing the security audit and the compliance improvement service to help the clients to get the international security certificates.
Reference:
https://www.ithome.com.tw/news/137953 https://www.nccst.nat.gov.tw/NewsRSSDetail?lang=zh&RSSType=news&seq=16401
https://www.mdeditor.tw/pl/29Sr/zh-tw https://www.securityweek.com/backdoor-found-rest-client-ruby-gem
https://github.com/rest-client/rest-client/issues/713 https://nvd.nist.gov/vuln/detail/CVE-2019-15224
https://www.zdnet.com/article/backdoor-found-in-webmin-a-popular-web-based-utility-for-managing-unix-servers/
https://nvd.nist.gov/vuln/detail/CVE-2019-15107 https://www.nccst.nat.gov.tw/NewsRSSDetail?lang=zh&RSSType=news&seq=16401
Compliance & Certification Services: It can improve the common product development life cycle management problems of enterprises. Customizing the product Security Management process, providing the security audit and the compliance improvement service to help the clients to get the international security certificates.
Reference:
https://www.ithome.com.tw/news/137953 https://www.nccst.nat.gov.tw/NewsRSSDetail?lang=zh&RSSType=news&seq=16401
https://www.mdeditor.tw/pl/29Sr/zh-tw https://www.securityweek.com/backdoor-found-rest-client-ruby-gem
https://github.com/rest-client/rest-client/issues/713 https://nvd.nist.gov/vuln/detail/CVE-2019-15224
https://www.zdnet.com/article/backdoor-found-in-webmin-a-popular-web-based-utility-for-managing-unix-servers/
https://nvd.nist.gov/vuln/detail/CVE-2019-15107 https://www.nccst.nat.gov.tw/NewsRSSDetail?lang=zh&RSSType=news&seq=16401






