The pandemic accelerates the cybersecurity of smart medical devices, the 8 key points of cybersecurity risk assessment
In recent years, the Taiwanese government has vigorously promoted the digital transformation of the health industry. In terms of the application of IoT devices combining big data analysis and AI computing technology to precision medical services, the medical market has gradually become an important battleground for domestic electronic device manufacturers. A variety of medical integration solutions are blooming, from doctor outpatient services to home care services. These data collection and data analysis can be carried out through the Internet, and the diagnosis results and medical orders can be transmitted in real time. It not only saves the queuing time required for patient registration, testing, and consultation, but also helps the integration and effective use of medical system resources.
In order to promote the wide application of smart medical care, the Taiwan Ministry of Health and Welfare has successively announced new rules for medical devices to provide a more flexible and convenient application channel for Information and Communications Technology (ICT) vendors or medical products integrating AI technology suppliers. These new rules also help software-based medical solutions to quickly go to market and meet market demands. The "Guidance for Industry on Management of Cybersecurity in Medical Devices" announced in May 2021 also clearly stated that before the product is approved for launch, vendors need to provide relevant documents such as design, risk management and cybersecurity testing for review. Regarding the risk assessment content mentioned in the guidance, the following focuses on the cybersecurity assessment techniques and methods that enterprises can follow or apply, and share them with medical device developers as a reference for the "Cybersecurity Risk Management Plan".
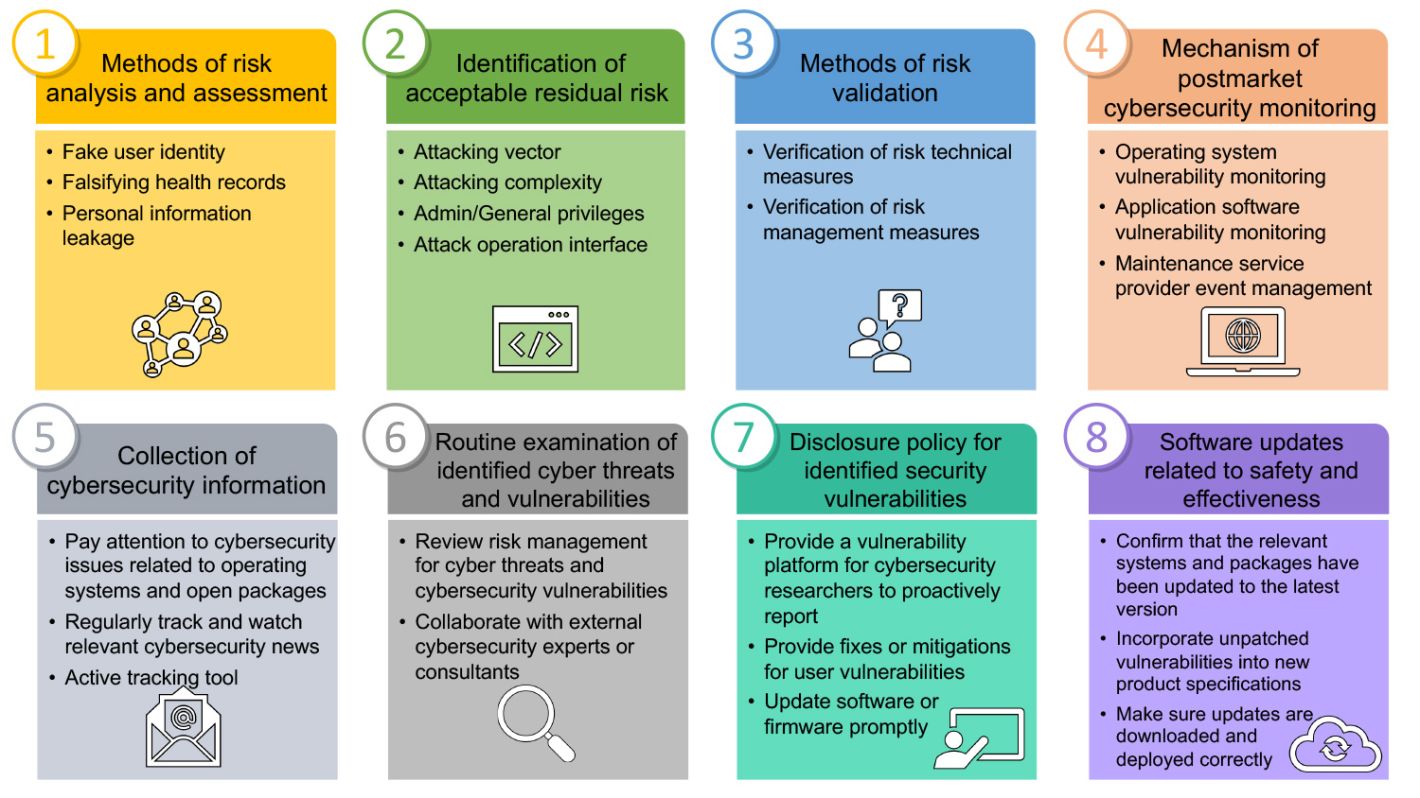
1. Methods of risk analysis and assessment
In order to ensure the effectiveness and security of medical device, medical device developers need to refer to the ISO 14971 medical device risk management standard to assess related risks. In the face of cybersecurity attacks, medical device developers need to consider the possible security threats in information processing, including fake user identity, falsifying health records, and personal information leakage. Traditional personal medical devices such as blood pressure machine and blood glucose machine that only provide simple measurement functions usually do not have a user identification mechanism. However, in order to meet the needs of smart medical care, the functions of personal health records and big data analysis for diagnosis are bound to be added. Therefore, medical device developers need to identify the user's identity, network storage method and data transmission mechanism, etc., all of which should be listed as assessment items in risk analysis.
2. Identification of acceptable residual risk
If medical device transmits personal health information or diagnostic results through Bluetooth, WiFi and other connection technologies, It should be assessed according to the cybersecurity risk factors faced by different transmission methods, such as attack vector, attack complexity, access authority and operation interface. Also, the acceptable residual risk should be determined during the development process. This part can refer to the assessment benchmark of Common Vulnerability Scoring System (CVSS). Through the assessment or simulation of network attacks by cybersecurity experts, the priority of dealing with risks can be determined according to the possibility of the occurrence of attacks, so as to help developers effectively respond and control.
3. Methods of risk validation
For the cybersecurity risk activities included in the risk analysis results, medical device developers should propose appropriate technical or management measures for verification. For example, as mentioned above, medical devices may face the risk of tampering and theft of health records in a networked environment. Medical device developers should propose communication channels or data encryption mechanism for this risk, and ensure the effectiveness of their technical or management measures through actual verification operations. If the product itself cannot provide an encryption mechanism due to limited technology and application scenarios, the manufacturer should still provide management measures to reduce the possibility of risk occurrence, such as: providing user message prompts when transmitting data, or adding precautions for data transmission in the user manual.
4. Mechanism of postmarket cybersecurity monitoring
In the past, the post-marketing services of medical devices were mainly based on hardware repair and maintenance. However, for devices with networking services, the operating system or development platform, application software, cloud service, and outsourced or self-developed monitoring mechanism are also items that must be continuously updated. Therefore, during the development process, it should be considered that the update of operating system, software and maintenance should be included in the scope of post-marketing services, so as not to fail to respond effectively when the post-market products involve cybersecurity vulnerability or accidents.
5. Collection of cybersecurity information
As open source packages are widely used by medical device developers, their devices are also vulnerable to open source packages vulnerabilities. Therefore, medical device developers must pay attention to whether there are new security issues in the operating system and open source packages, and take appropriate coping mechanisms. In this regard, it is recommended that medical device developers can regularly track and watch cybersecurity news, and can also use tools to actively track major cybersecurity news platforms and vulnerability databases. Filtering product-related vulnerabilities with the help of tools can save developers time in screening relevant information, and effectively utilize human and time resources in vulnerability verification and repair.
6. Routine examination of identified cyber threats and vulnerabilities
The above-mentioned cyber threats analyzed during the development process and the cybersecurity vulnerabilities identified after the launch must be regularly checked whether the existing technologies or control measures are effective and reasonable. It is suggested that medical device developers can review the risk management and control measures of cyber threats and cybersecurity vulnerabilities while conducting functional inspections according to the product planning and development schedule. For medical device developers who lack cybersecurity professionals, a better approach is to cooperate with external cybersecurity experts or consultants, and select applicable control measures and procedures. Consultants with experience in cybersecurity assessment can assist in the preparation of cybersecurity inspection documents and records required by regulations for the competent authorities to review.
7. Disclosure policy for identified security vulnerabilities
When medical device developers are faced with cybersecurity vulnerabilities, they do not actually understand the serious consequences that these vulnerabilities may bring. However, cybersecurity vulnerabilities are as difficult to eradicate as the infectious source of Covid-19. No operating system or application software can claim to be flawless. Once someone with intentions wants to destroy the device, they can spend a lot of time and manpower to discover the vulnerability and find the breach. If these cybersecurity vulnerabilities are not taken seriously, they will be as difficult to control as the pandemic. And they not only damage the company's reputation, they may even cause human harm and lead to the company facing claims. Many well-known international companies have begun to actively face cybersecurity vulnerabilities, and provide channels for cybersecurity researchers to report product vulnerabilities, while assisting users to correct product vulnerabilities through software or firmware updates to reduce the damage caused by cybersecurity vulnerabilities.
8. Software updates related to security and effectiveness
Providing safe and effective software for continuous maintenance and operation is a major subject for future smart medical services. Teams with development capabilities should confirm whether the relevant systems and packages have been updated to the latest version during routine product revisions, and consider how the vulnerabilities that cannot be patched in time can be incorporated into new product specifications. Device manufacturers who outsource development or maintenance operations should also properly plan the responsibilities and obligations of outsourced vendors to ensure safe and effective software continuous maintenance operations and software supply chain security. In addition, medical device developers should provide software updates, and use the update "file signature" method to ensure that the update files can be downloaded, deployed and installed correctly.
More and more Netcom or information service providers are investing in the development of AI medical products or services. In addition to applying for medical devices based on government guidance, vendors should also assess medical devices, including the design and development of network and software services, as well as risk management, and use cybersecurity test results as supporting records. If the vendors can effectively perform network risk assessment during development, cybersecurity vulnerabilities discovered after the product is launched will be easier to grasp and more efficient to respond to.
Onward Security has the most complete cybersecurity assessment laboratory in Asia, with in-depth medical device cybersecurity technology expertise, and provides US FDA and EU MDR MDCG consulting and testing services for medical device cybersecurity. We have assisted many domestic and foreign vendors to pass the cybersecurity regulations of medical devices. In addition, our self-developed automated tools, HERCULES SecDevice and SecSAM, can support software vulnerability testing and SBOM functions required for product development, which can effectively assist medical device developers to build "Cybersecurity Risk Management Plan" and conduct cybersecurity assessment and testing.






