Security Incident
15.Dec.2021
Avoid falling victim to the worst zero-day vulnerability in recent years! Understanding what Apache log4j is? How to patch the CVE-2021-44228 vulnerability
What is Apache log4j
The Apache Foundation issued a serious vulnerability warning about log4j earlier. Log4j is a common open-source logging framework. Many developers use it to log activity in their applications. The reported remote code execution vulnerability (CVE-2021-44228) exists in all versions of log4j 2.x to 2.16.0 (released 2021/12/13). This vulnerability is called "Log4Shell". It allows an unauthenticated remote attacker to execute arbitrary code by writing system logs with remote JNDI API calls, thereby gaining control of the target system. The severity of the vulnerability is rated at 10 out of 10 according to Common Vulnerability Scoring System (CVSS) v3.1. Since log4j is widely used in different commercial applications and services, including Minecraft, Elasticsearch, and VMware VCenter, the log4j vulnerability is arguably one of the worst in recent history.
Check for Apache log4j vulnerability by verification service
If you're not certain whether your existing services or products are affected by this security vulnerability, the HERMAS research team of Onward Security has successfully reproduced the security vulnerability of Log4Shell and started to provide customer security vulnerability verification service. We can assist in detecting whether your systems and products are affected by this security vulnerability.Identify Apache log4j risks with SecSAM
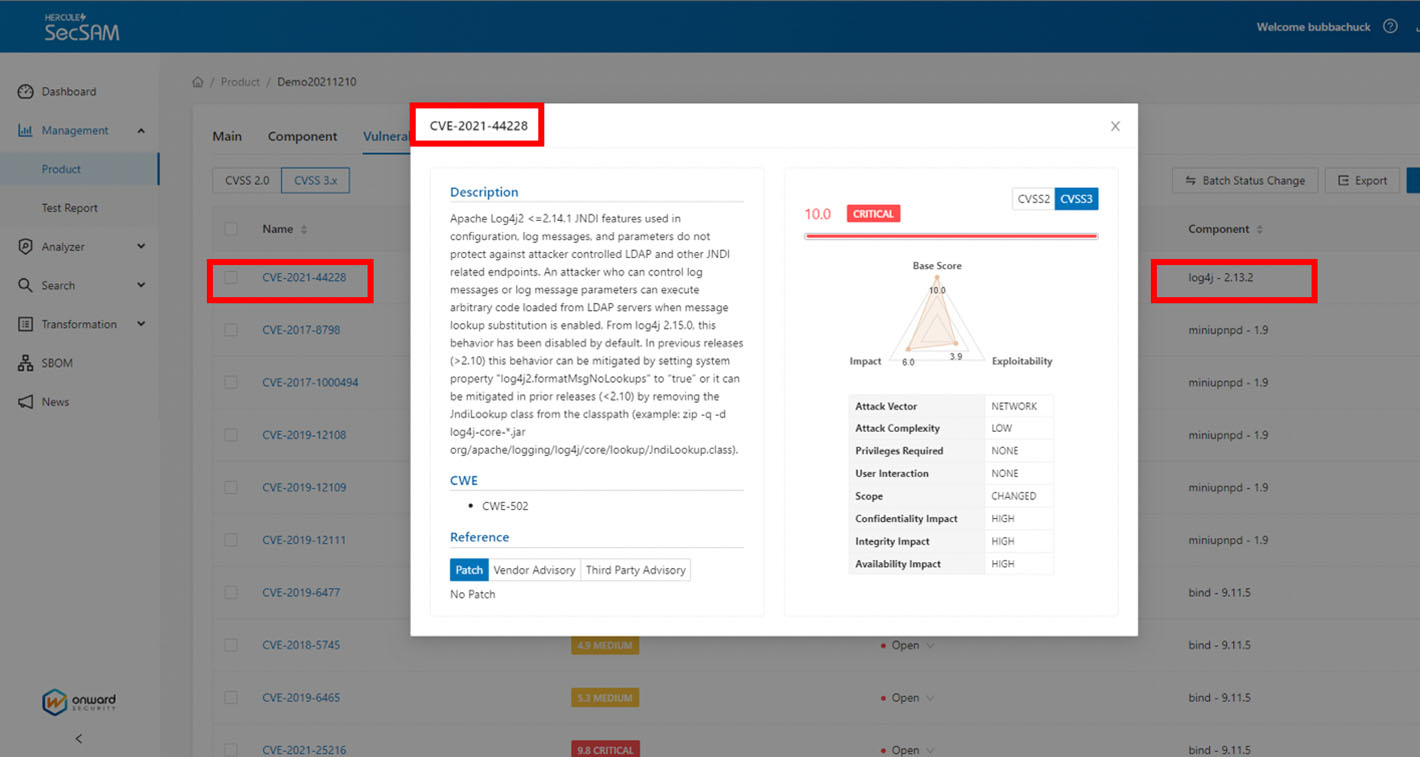
By using HERCULES SecSAM, you can create an Software Bill of Materials (SBOM) for your product and check if the component that contains this vulnerability is used. You can also use the firmware scanning automatic analysis software to confirm whether this risk component exists in the firmware.
Vendor Advisory

(Identify potential risks in products through SecSAM)
Mitigation solutions
When HERCULES SecSAM detects an affected version of Log4j after scanning, you can upgrade Log4j to a version above 2.16.0 (inclusive). You can also refer to the following vulnerability mitigation solutions compiled by SecSAM.Vendor Advisory
- [oss-security] 20211210 Re: CVE-2021-44228: Apache Log4j2 JNDI features do not protect against attacker controlled LDAP and other JNDI related endpoints
- https://logging.apache.org/log4j/2.x/security.html
- https://security.netapp.com/advisory/ntap-20211210-0007/
- [oss-security] 20211210 Re: CVE-2021-44228: Apache Log4j2 JNDI features do not protect against attacker controlled LDAP and other JNDI related endpoints
- https://logging.apache.org/log4j/2.x/security.html
- https://security.netapp.com/advisory/ntap-20211210-0007/






