Product Security
20.May.2020
How to balance the agility and security of product development? About the complementarity of DevSecOps and automation
The importance of DevSecOps can be learned from the past. In 2019, a tragic case was that Facebook once again faced the data leak. More than 267 million Facebook user profiles were exposed on the online database of the Dark Web, including names, IDs and phone numbers. These users may be subject to cyber attacks of spam or phishing emails, which caused Facebook to suffer a loss of credit and a stock price crash[1].
For many companies, Cloud and DevOps are the key technology engines driving enterprise business development. IT, security and developing staff in the enterprise all know that in Cloud and DevOps environments, there are a lot of sensitive messages (such as secret key) that need to be protected. Most people have security awareness, but we can still see many incidents that leak important information.
In the era of big data with the rapid development of the Internet, many enterprises have practiced "agile" thinking and actions. This is a signal that needs to face different risks at the same time and is constantly being verified. More and more consumers, regulators and markets have discovered that the cost of data leakage caused by this is high and unacceptable. In fact, many data breaches can be prevented in advance. Through the promotion of the concept of DevSecOps and the assistance of automation systems, these problems and risks would be effectively reduced, and the security and quality of the output can be ensured. However, it is not so easy to introduce DevSecOps. This article will explain the key issues when implementing DevSecOps and how to achieve this goal efficiently and beneficially.
For many companies, Cloud and DevOps are the key technology engines driving enterprise business development. IT, security and developing staff in the enterprise all know that in Cloud and DevOps environments, there are a lot of sensitive messages (such as secret key) that need to be protected. Most people have security awareness, but we can still see many incidents that leak important information.
In the era of big data with the rapid development of the Internet, many enterprises have practiced "agile" thinking and actions. This is a signal that needs to face different risks at the same time and is constantly being verified. More and more consumers, regulators and markets have discovered that the cost of data leakage caused by this is high and unacceptable. In fact, many data breaches can be prevented in advance. Through the promotion of the concept of DevSecOps and the assistance of automation systems, these problems and risks would be effectively reduced, and the security and quality of the output can be ensured. However, it is not so easy to introduce DevSecOps. This article will explain the key issues when implementing DevSecOps and how to achieve this goal efficiently and beneficially.
Culture is the core spirit of the DevSecOps
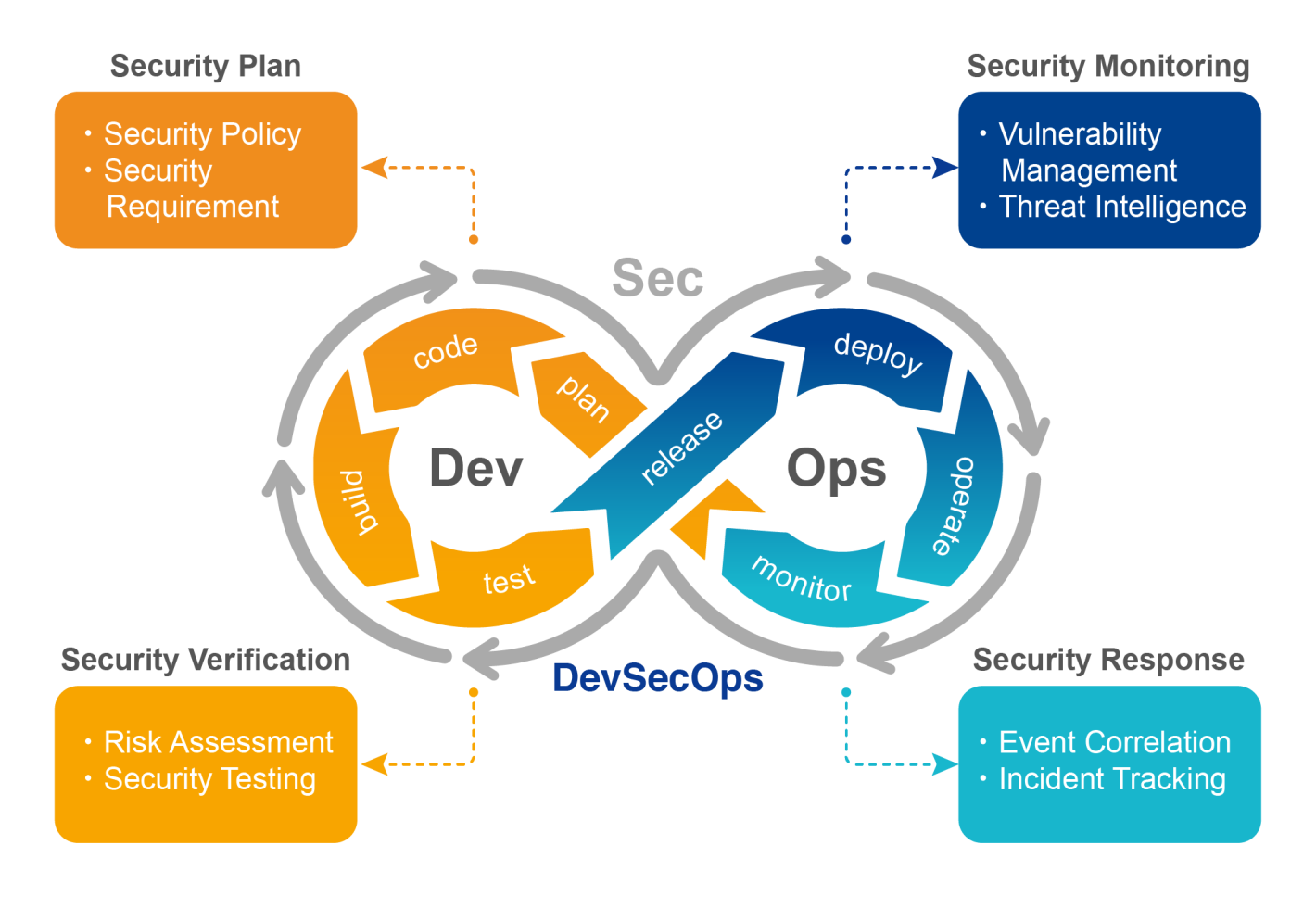
DevSecOps is an abbreviation of Development, Security, and Operations. The basic idea of DevSecOps is that multiple cross-department collaborators (including solutions, developing, testing, IT, maintenance, etc.) must have the security concept development and correctly understand the agile practices and meaning of DevOps. In other words, DevSecOps is a group practice. Its core concept is, "Security is the responsibility of all members of the entire team, and it needs to run through every link in the entire software life cycle." In short, DevSecOps regards the realization of security as a culture. Therefore, the most important thing is to integrate the security elements in DevSecOps with the interests of each team, and ultimately must be assimilated into the corporate culture[2].

DevSecOps regards the realization of security as a culture
Carry out cybersecurity by teamwork
A major focus of DevSecOps is to allow the development team, Operations and maintenance (O&M) team and security team to cooperate with each other, enabling them to look at problems objectively from the other sides’ perspective instead of confrontation or containment in the past. O&M engineers usually do not know much about development or security, and developers are not good at O&M or security. DevSecOps hopes to break this gap and divide the authority and responsibility of "doing cybersecurity". The security team will participate and take responsibility for communication and coordination, letting everyone proactively practice information security together, face and deal with vulnerabilities together, and make products safer together[2].
Automation system can lower the threshold when implementing DevSecOps in developing software
According to IBM's research statistics, the cost of fixing security issues after product release is 4 to 5 times higher than that during the design phase. If the problem is fixed at the maintenance stage, its cost will reach or even exceed 100 times[3]. Therefore, DevSecOps needs to be involved in the early stage of software development, including the education and training on security awareness and security development specifications for development and maintenance staff, security requirements (non-functional requirements) import, and preliminary software code audit. The DevSecOps approach seems to add work items to security, but finding problems in advance can greatly reduce development and maintenance costs throughout the product lifetime.
In addition, the security work of DevSecOps is often mistaken for development bottlenecks, such as a large number of security requirements, a long testing and evaluation times, or difficulty in implementing security monitoring[3]. In fact, this is because most companies are reluctant to invest manpower and do not know how to automate, resulting in failure to integrate DevSecOps with existing processes and cultures. DevSecOps adopts a rapid iterative development method, allowing application systems to realize the value and security attributes they should have in the shortest period. Comparing to other information security methodologies[4], it is faster and more flexible. The automation adoption can assist the team to achieve the DevSecOps easily, and makes it more valuable and efficient.
In addition, the security work of DevSecOps is often mistaken for development bottlenecks, such as a large number of security requirements, a long testing and evaluation times, or difficulty in implementing security monitoring[3]. In fact, this is because most companies are reluctant to invest manpower and do not know how to automate, resulting in failure to integrate DevSecOps with existing processes and cultures. DevSecOps adopts a rapid iterative development method, allowing application systems to realize the value and security attributes they should have in the shortest period. Comparing to other information security methodologies[4], it is faster and more flexible. The automation adoption can assist the team to achieve the DevSecOps easily, and makes it more valuable and efficient.
Accurately grasp security issues to remove serious vulnerabilities in real time
In many cases, in order to accelerate product development and time-to-market, the software of the product is not completely self-developed, but rather is collected and integrated a large number of pre-compiled components and libraries from Open Source or libraries, such as GitHub, SourceForge or Docker Hub[5]. Since the proportion of self-programmed code in the existing software is greatly reduced, the focus of security risks has also shifted. Most security risks can be identified through these public libraries, known vulnerabilities and misconfigurations of third-party components. The product can be put into production after the problem is solved. From a security point of view, identifying known vulnerabilities in Open Source is much easier than discovering unknown vulnerabilities in self-programmed code. The easiest and fastest way is to compare Open Source or third-party components with the vulnerability database.
In addition to the automated security vulnerability analysis mentioned above in the design and development phase, the support of third-party security testing tools is also a key player. In order to ensure that most risks are removed before the product release, how to efficiently carry out security confirmation and vulnerability verification is an important checkpoint for the development team to achieve secure development.
In addition to the automated security vulnerability analysis mentioned above in the design and development phase, the support of third-party security testing tools is also a key player. In order to ensure that most risks are removed before the product release, how to efficiently carry out security confirmation and vulnerability verification is an important checkpoint for the development team to achieve secure development.
Security culture needs to run through the entire DevSecOps process
In the maintenance stage after the product is released, the most important thing is to continuously monitor and deal with internal and external security threats at any time, for example, whether the external server has been attacked, whether the product vulnerability is publicly exposed on the Internet without being informed or whether the latest Open Source vulnerabilities have been discovered. The last thing is to pay attention to the latest network attack trends so as to take corresponding security protection measures as soon as possible.
Based on past experience, the teams usually lack communication and cooperation at this stage, especially for the product security issues. The O&M team is unable to establish an effective and clear division of responsibilities with the development team. Plus, the main responsibilities of the two departments are different. As a result, when the product security problem occurs, the development team eventually is wheeled out to deal with the problem and the O&M team could not help. The best solution at this time is to establish a set of standard procedures (SOP) that clearly states the assignments and responsibilities of each team as well as the handling process when the event occurs. Of course, one of the key points is that a dedicated team and manpower are needed to coordinate and the security team is the most suitable for this mission[6][7].
The relevant teams can therefore accumulate long-term experience in communication, coordination and handling of security incidents, and feed back the security information to the development team. It not only can make the overall process and measures more perfect, but also can predict or prevent the occurrence of network attacks or product vulnerabilities. This is also an important segment and the spirit of DevSecOps.
Based on past experience, the teams usually lack communication and cooperation at this stage, especially for the product security issues. The O&M team is unable to establish an effective and clear division of responsibilities with the development team. Plus, the main responsibilities of the two departments are different. As a result, when the product security problem occurs, the development team eventually is wheeled out to deal with the problem and the O&M team could not help. The best solution at this time is to establish a set of standard procedures (SOP) that clearly states the assignments and responsibilities of each team as well as the handling process when the event occurs. Of course, one of the key points is that a dedicated team and manpower are needed to coordinate and the security team is the most suitable for this mission[6][7].
The relevant teams can therefore accumulate long-term experience in communication, coordination and handling of security incidents, and feed back the security information to the development team. It not only can make the overall process and measures more perfect, but also can predict or prevent the occurrence of network attacks or product vulnerabilities. This is also an important segment and the spirit of DevSecOps.
Benefits of adopting the DevSecOps: shorten incident processing time
Establishing the DevSecOps process can effectively integrate the communication channels between the development, security and O&M teams to shorten the response time of the incident. This will be the most direct and obvious benefit. According to DigiCert’s survey report, 98% of companies are using or planning to adopt DevSecOps[8]. According to another statistics, the company that have not implemented DevSecOps takes 174 days to fix a vulnerability found when using dynamic analysis in production, but those who have implemented DevSecOps do it in just 92 days. The gap is almost double the time. In addition, for DevSecOps companies, 53% of all the vulnerabilities found can be fixed within 10 days; for non DevSecOps companies, only 5% can be fixed within 10 days[9]. These gaps in numbers are proof that the introduction of DevSecOps can speed up the processing of vulnerabilities or incidents. In other words, this of course has the advantage of reducing the related costs.
HERCULES SecFlow with automation features meets agile development and improves security
HERCULES SecFlow, developed by Onward Security, provides automated auxiliary functions for DevSecOps processes, allowing users to speedily and easily establish information security communication channels and mechanisms. It can assign the corresponding rights and responsibilities to the relevant teams. By assigning tasks, reviewing and reporting functions, all teams can quickly adapt to the concept of product security development. Through the SecFlow policy module, the security team can publish the security-related information and the reminder notes about the secure code development to the relevant staff (such as R & D team or O&M team). A series of assignments, sign-off procedures, as well as providing the latest information can fully strengthen the security awareness of each team.
SecFlow has complete vulnerability management functions. In addition to importing a variety of third-party security test reports and providing vulnerability tracking tools, it help users establish the correspondence between products, components and security information. The powerful data collector aggregates and analyzes a large amount of international vulnerability data and real-time security news as security information. They automatically associate with the products through machine learning to promptly identify vulnerability, security news and security incidents related to users' own products. This allows the relevant teams to keep track of the security risk level of the products and to immediately remove or fix serious vulnerabilities. Finally, proactive email alerts and mobile App enable security managers to accurately grasp the vulnerability information and processing progress to ensure that each incident has been corrected or improved.
SecFlow has complete vulnerability management functions. In addition to importing a variety of third-party security test reports and providing vulnerability tracking tools, it help users establish the correspondence between products, components and security information. The powerful data collector aggregates and analyzes a large amount of international vulnerability data and real-time security news as security information. They automatically associate with the products through machine learning to promptly identify vulnerability, security news and security incidents related to users' own products. This allows the relevant teams to keep track of the security risk level of the products and to immediately remove or fix serious vulnerabilities. Finally, proactive email alerts and mobile App enable security managers to accurately grasp the vulnerability information and processing progress to ensure that each incident has been corrected or improved.
The combination of SecFlow and DevSecOps
SecFlow plays a key role in the automation of DevSecOps. There is no manual intervention is required in the team information exchange and security information collation. There is also no time-consuming and labor-intensive work such as checking the product vulnerabilities and Open Source management. Its advanced data collect and analyze algorithms can automatically correlate and filter the security vulnerabilities or events so as to deal with them accurately. Through the real-time warning mechanism, it helps users rapidly handle and track security issues to feed the security information at each stage back to all teams. Some people say that it is difficult to maintain a balance between security and agile development, but as long as using SecFlow it is possible to balance both, because SecFlow allows the implementation of DevSecOps to be fully adapted to each team, rather than to cause a greater burden.
About HERCULES SecFlow
HERCULES SecFlow is a "product security management system" for product development related teams. Based on the principle of Secure by Design, it provides an automated system management mechanism to manage and track each stage of DevSecOps, as well as the required security processes and measures. It enables the development, security and O&M teams to work in tandem with each other so as to quickly establish a secure software development process. The SecFlow provides information on security vulnerabilities and security incidents in real time. Its automated vulnerability analysis and management function can ensure the security of products and third-party packages, reduce the security risk derived from the software development process, improve overall security response and processing efficiency, and avoid dispute litigation arising from product security issues.
Reference:
[1] 數位時代(12, 20, 2019), 2.67億筆個資遭公開下載!Facebook用戶資料外洩又爆一樁醜聞, https://www.bnext.com.tw/article/55989/267-million-phone-numbers-exposed-online
[2] Red Hat, What is DevSecOps?, https://www.redhat.com/en/topics/devops/what-is-devsecops
[3] KKNews, 大膽預測:現有IT開發和運營或將顛覆, https://kknews.cc/zh-tw/tech/mmmgqa9.html
[4] VERITIS(APRIL 10, 2018), Early Automation: A Key Requirement for DevSecOps Success, https://devops.com/early-automation-key-requirement-devsecops-success/
[5] 知呼, DevSecOps:應當做好的十件事, https://zhuanlan.zhihu.com/p/44691252
[6] Neil MacDonald, Mark Horvath, Ayal Tirosh, 16 November 2017, Integrating Security Into the DevSecOps Toolchain
[7] GSA, Understanding the Differences Between Agile & DevSecOps - from a Business Perspective, https://tech.gsa.gov/guides/understanding_differences_agile_devsecops/
[8] DgiCert(July 19, 2017), DigiCert Survey Shows Enterprises Integrating Security Teams into DevOps, https://www.digicert.com/news/survey-integrating-security-into-devops/
[9] https://www.csoonline.com/article/3245748/what-is-devsecops-developing-more-secure-applications.html






