Enterprise Security
19.May.2020
The stay-at-home economy thrives during the pandemic, how to stop hackers and protect online transactions
Starting from February 2020, the COVID-19 pandemic has created a whirlwind of stay-at-home economy in the market. The usage rate of e-commerce platforms and video streaming platforms has increased significantly. However, many information security issues are hidden in online trading websites or platforms. As early as 2016, a security researcher had notified Uber of a security vulnerability that could allow attackers to brute force guessing to obtain Uber coupon codes with limited usage and value in the US dollar between $5,000 to $25,000[6]. This shows that if the online trading website has security vulnerabilities during the process of membership registration (filling in personal information), login, purchase and payment, the website may be misused by malicious attackers or be stolen important data such as personal and financial information.
The Open Web Application Security Project (OWASP) is a non-profit organization.[1] In the early days, it mainly focused on researching and publishing website application security. The OWASP Top 10 is a guide with the considerable reference value in the industry. Some system platforms that offer online trading have inherent vulnerabilities. For example, the well-known e-commerce platforms Magento, Joomla kit, and WordPress kit all have been found to have SQL injection vulnerability that the database information can be stolen.[2][3][4]. SQL injection is the number one security risk in OWASP TOP 10: Injection.[5]。
In the above Uber case, attackers can obtain discount coupon codes through repeated brute-force guesses. Such vulnerability is the second security risk in OWASP TOP 10: Broken Authentication[7]. Website developers can change the authentication mechanism to Multi-Factor Authentication (MFA). For example, adding reCAPTCHA v3 as a defense mechanism on the page that may be attacked can invalidate most automated attack programs. Another approach is to add account lockout mechanisms to limit the number of times users can log in within a period of time. If the number exceeds the limit, it will take a while for users to log in again.
However, today's websites often claim that there will be no security vulnerabilities because of the use of HyperText Transfer Protocol Secure (HTTPS). In fact, it only avoids the third security risk in OWASP TOP 10: Sensitive Data Exposure[8]. Through secure encrypted connection, it can avoid Man-in-the-middle attack, eavesdropping on user traffic, obtaining account number, password and credit card number, but can not solve the above Broken Authentication problem.
It can be learned from the aforementioned actual cases and the common attack methods in OWASP that these will all lead to security problems in online transactions. In recent years, attackers have often used Distributed Denial of Service Attack to try to paralyze the target website, resulting in users unable to connect to the website, and causing service interruption and financial loss. At the beginning of 2017, many securities firms that provided online orders received blackmail letters from hackers, and dealers who received threatening letters immediately reported the case to Financial Supervisory Commission (FSC). At the same time when the letter was received, some of the dealers have subjected to exploratory DDoS attacks by hackers, causing some transactions to be suspended. The hacker’s letter indicated that they will be subject to subsequent DDoS attacks if they do not pay. Under the threat, the small and medium-sized dealers fear that the online trading system will suffer attack, so they pay the hackers privately, but there are still many securities firms that have suffered DDoS attacks. Therefore, the most effective method is to establish DDoS defense and emergency operating procedures, and hold DDoS attack emergency drills every year, so as to reduce the time and damage suffered by DDoS attacks.
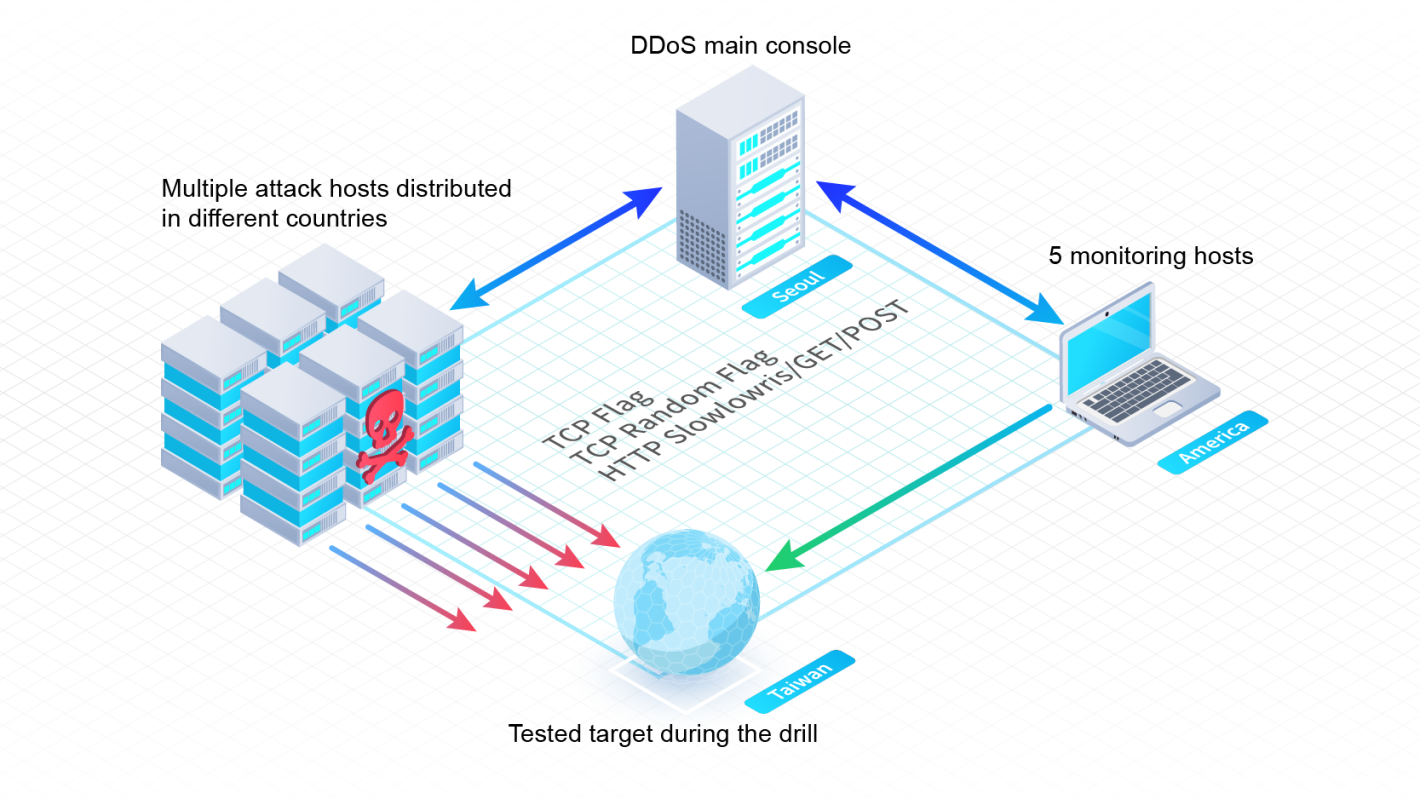
Protecting users' personal information and making websites operate normally is crucial. The operators need to regularly perform penetration testing and DDoS drills for their online trading websites, so as to ensure that the current security protection mechanism can operate properly to prevent attacks. The security team of Onward Security is able to simulate a real hacker attack, simultaneously control more than 1,000 hosts from 34 different countries around the world to conduct DDoS attacks, and simultaneously perform multiple Layer 4 and Layer 7 cyber attacks. This simulation allows self-defining execution time, website traffic, number of connections and packet content according to customer needs, and reaching a maximum traffic up to 500G to 1T at the same time. Whether it is to verify the system tolerance on DDoS attacks or to conduct stress tests on the number of user connections, Onward Security can provide customers with the most complete website security testing services to solve the various security problems faced by customers.
[1] https://owasp.org/
[2] hehackernews.com/2019/03/magento-website-security.html
[3] https://thehackernews.com/2017/05/joomla-security-update.html
[4] https://thehackernews.com/2017/06/wordpress-hacking-sql-injection.html
[5] https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017_A1-Injection
[6] https://thehackernews.com/2016/06/unlimited-uber-free-rides.html
[7] https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017_A2-Broken_Authentication
[8] https://owasp.org/www-project-top-ten/OWASP_Top_Ten_2017/Top_10-2017_A3-Sensitive_Data_Exposure






