OT Security
19.Aug.2020
Cybersecurity defense practices for smart factory (Part 1)
Deployment errors will lead to cybersecurity crisis
In recent years, the government has been vigorously promoting Industry 4.0, also known as Smart Factory. Its focus is on the intelligence of the production line, which needs to integrate existing IT and OT technologies, and use numerous IoT devices, so as to meet the rapidly changing needs of customized manufacturing. In order to optimize the production process, it is an inevitable trend to adopt and deploy a large number of cybersecurity equipments. However, no matter how good cybersecurity products are (such as gateway firewalls), they may lose their defensive capabilities and become a cybersecurity breach when they are deployed incorrectly. Most hackers prefer to set their sights on "easy" targets, and then attack the targets or turn them into a Botnet for their own use. The obvious errors in deployment are bound to make hackers think that they are "easy" targets. This will attract hackers and cause 21% of sensitive information in the global manufacturing industry to leak [2]. This article takes a practical perspective as the starting point to discuss the defense practice in the huge challenge.
Understanding the compliance architecture first, before building a smart factory
Based on the ISO/IEC 62443 standard specification, the U.S. Department of Homeland Security [3] recommends the following configuration for the practical implementation structure in the factory, which can be divided into five to six levels:
1. Field device level (Level-0: Field I/O Devices)
This level refers to the sensors and actuators deployed in the production line. According to different functional requirements, it can include but is not limited to: relay, signal and interface converter, control valve, pump, motor, fan, light, conveyor belt, robotic arm, cutting machine, molding machine, automatic elevator and stacker, CCTV in the factory, etc.2. Control level (Level-1: Basic Control and Safety Protection)
Under standard specification, this level should also be well protected. Many Remote Terminal Unit (RTU), Human Machine Interface (HMI) and Programmable Logic Controller (PLC) [4] are deployed at this layer to form the industrial Internet of Things (IIoT) with Distributed Control Systems. As a key device, PLC also contains numerous functional modules connected to various I/O devices of level 0 for programmable control.3. Supervision and regional process control level (Level-2: Supervisory and Area Process Control)
Integrating the various data of the first two levels into the Supervisory Control and Data Acquisition (SCADA) system can collect, monitor and analyze big data on the production line, and even perform artificial intelligence computing and factory-owned cloud computing to build a digital neural network in the smart factory.4. OT manufacturing maintenance and operation level (Level-3: Site Manufacturing Operations and Control)
The main configuration is to integrate the information of multiple SCADA systems such as maintenance workstations and long-term log inventory machines. Practically none of the three levels mentioned above should have the ability to connect to the external network. The acquisition and integration of external network resources should be carried out at this level, and then the resources are distributed to the operation layer and control layer that need to use these resources. In addition, this level can also split into Level-3.5 to configure the demilitarized zone (DMZ) between IT and OT so as to access the shared resources, including update file delivery server, intranet time calibration server, etc. As for the large-scale factory, it is even necessary to configure internal Domain Name System (DNS) in the DMZ in order to use the AD (Active Directory Services) server for asset registration and management. Furthermore, the DMZ at this level should not serve the external network. IT conducts the unidirectional OT remote monitoring only through Jump Server.5. Enterprise IT management level (Level-4: Enterprise IT Zone)
This level is to build an enterprise business zone isolated from the physical network of the factory. The zone is provided for the office uses, including the shared file server, enterprise resource management (i.e. ERP, CRM and the aforementioned AD server), printer, internal mail server, and VPN server connected to different offices in very remote locations via the intranet. It may also include office cybersecurity management systems, Security Information Event Management (SIEM), etc. to support the daily operations of OA business units such as corporate business, customer service, administrative management, product development and design, financial and tax management, and so on. The US Department of Homeland Security also recommends that this level should be split into two sub-levels: a Site Business Planning and Logistics Network and an enterprise IT management. Besides, there is a zone outside the IT management, called the demilitarized zone between the corporate intranet and the Internet. It is configured to provide public browsing website, file server, domain server, mail server, etc.![Configuration Diagram A: Industry 4.0 secure network architecture recommended by the US Department of Homeland Security [3]](https://www.onwardsecurity.com/upload/news_resource_blog_b/ALL_news_resource_blog_22J18_pkjMvx7vg3.jpg)
Configuration Diagram A: Industry 4.0 secure network architecture recommended by the US Department of Homeland Security [3]
![Configuration Diagram B: Industry 4.0 secure network architecture recommended by the US Department of Homeland Security [3]](https://www.onwardsecurity.com/upload/news_resource_blog_b/ALL_news_resource_blog_22J18_NM1OHsrZTE.jpg)
Configuration Diagram B: Industry 4.0 secure network architecture recommended by the US Department of Homeland Security [3]
![Example: A layered architecture of smart manufacturing industrial control from Taiwan Power Company’s smart grid cybersecurity design [5]](https://www.onwardsecurity.com/upload/news_resource_blog_b/ALL_news_resource_blog_22J18_UDASNJxTFP.jpg)
Example: A layered architecture of smart manufacturing industrial control from Taiwan Power Company’s smart grid cybersecurity design [5]
The implementation framework under such specification is bound to be more complicated than Industry 3.0. The known cybersecurity issues in the existing framework may occur again in the future. The increasingly complex environment will be a huge challenge for IT and OT maintenance teams.
Common mistakes in deployment
The following [6] part refers to the implementation framework described in the previous section:
- Confusion and misplacement of the implementation architecture makes detection and monitoring difficult
- Level-0 to Level-3 devices are directly exposed to the external network that are vulnerable to attacks
- Level-3.5 services exposed to the external network have no security settings or its setting is modified to a safe value
- Enable or install unnecessary features
- Use the default account password of industrial control products
- Publicly display the unnecessary information and program debugging information
- Disable the security protection function
- Upgraded industrial control products do not have proper security settings
- Use outdated industrial control products that are no longer updated and maintained
- No detection modules or related security products for asset changes
- Unable to comply with the implementation structure due to using unqualified industrial control products that lack security settings
How did hackers invade?
Before the attack: Reconnaissance
Shodan.io[7], a well-known website in the cybersecurity industry, is a paid search engine used by cybersecurity personnel to conduct research and monitor basic information about connected devices around the world. The website can at least find out where the IPv4 is located in the world, which ports are open to the outside world, what clear text messages do the port receiving service respond? It also connects to Exploit-DB to check whether there are related CVE vulnerabilities and proof-of-concept programs for these vulnerabilities. Meanwhile, it can conduct statistics and generate reports based on the country, organization or ISP operator. Through it, researchers can report network usage to government agencies [8], and enterprise organizations can check the status of their own IPv4 on the external network or conduct cybersecurity checks during business transactions.
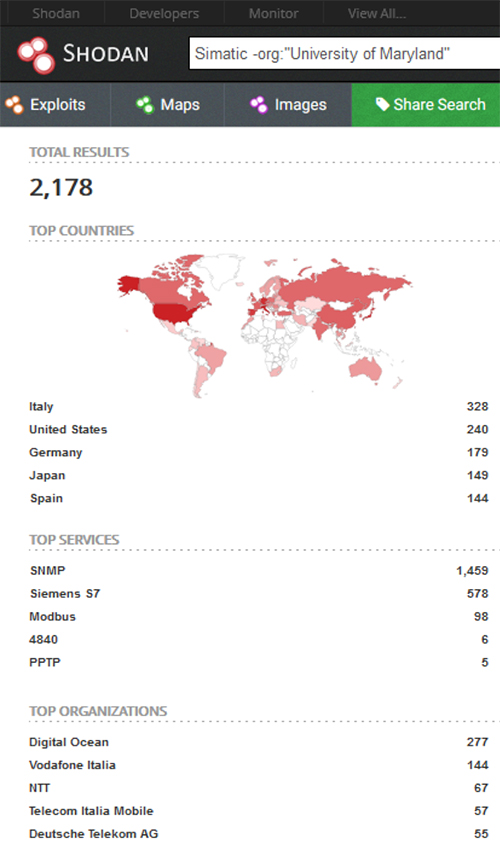
However, not only researchers, but also hackers use the Shodan search engine to find targets. Taking Siemens’ industrial control products as an example [9][10], a search on Shodan with the keyword "Simatic" in July this year showed that there were 2550 ports in the world (including 612 ports in the US, 13 IPv4 ports in Taiwan, 149 ports in Japan, 67 ports in China) that are marked with the names of Siemens industrial products in clear text. Further analysis of the composition of the global data, it includes a total of 372 HoneyPots about hacking behaviors researched by the University of Maryland in the US. After deducting the data of the University, Siemens SNMP service that should only be deployed on the intranet but is actually exposed on the Internet has 1,459 records, Siemens PLC module model S7 has 578 records, and Siemens Modbus that connects SCADA and RTU has 98 records. There are even HTTP ports in the data, which can access the web login page of the PLC module or routing gateway. If the deployer does not change the default account password, or a hacker uses Brute Force to crack the account password, someone may be able to control the PLC module or gateway. In fact, researchers can see some of SIMATIC modules too when searching with Shodan [12], and can directly access them without a password such as viewing intranet information or HMI information.
Shodan.io search query page
![Search query result page: Access to Siemens SIMATIC PLC module without password [12]](https://www.onwardsecurity.com/upload/news_resource_blog_b/ALL_news_resource_blog_22J18_hWjounKCY3.jpg)
Search query result page: Access to Siemens SIMATIC PLC module without password [12]
Exploit-DB: Proof-of-concept programs for Siemens industrial control products
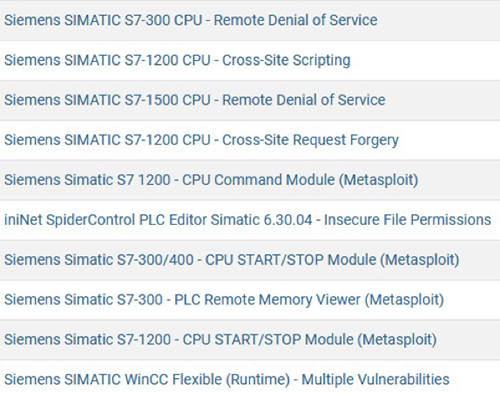
The above is just an example of Siemens industrial control products. More information on other industrial control products, IT products and IoT products can be found on Shodan. The CVE vulnerability items it contains are even more diverse. Besides, the proof-of-concept programs of Exploit-DB are only the tip of the iceberg, because the underground market, hidden on the dark web where hackers trade with each other, is full of attacks and control type malwares.
References:
[1]《WHITE PAPER : Smarter Security for Manufacturing in The Industry 4.0 Era - Industry 4.0 Cyber Resilience for the Manufacturing of the Future》Broadcom、Symantec. URL:https://docs.broadcom.com/doc/industry-4.0-en
[2]《2019 GLOBAL DATA RISK REPORT FROM THE VARONIS DATA LAB》Varonis。URL:https://info.varonis.com/hubfs/Varonis%202019%20Global%20Data%20Risk%20Report.pdf#page=20
[3]《Recommended Practice: Improving Industrial Control System Cybersecurity with Defense-in-Depth Strategies》Industrial Control Systems Cyber Emergency Response Team, CISA, Department of Homeland Security. URL:https://us-cert.cisa.gov/sites/default/files/recommended_practices/NCCIC_ICS-CERT_Defense_in_Depth_2016_S508C.pdf
[4]《Programmable Logic Controllers - Security Threats and Solutions》Texas Instruments. https://www.ti.com/lit/an/spraco8/spraco8.pdf
[5]《Smart Grid: Security》. URL:https://smartgrid.taipower.com.tw/en/page.aspx?mid=15
[6]《OWASP Top Ten》OWASP. URL:https://owasp.org/www-project-top-ten/
[7]《Shodan Help Center: Navigating the Website》Shodan.io. URL:https://help.shodan.io/the-basics/navigating-the-website
[8]《US government warns over vulnerable control systems》BBC UK. URL:https://www.bbc.com/news/technology-20984827
[9]《CVE Details: Siemens Products》CVE Details. URL:https://www.cvedetails.com/product-list/product_type-/vendor_id-109/firstchar-S/page-3/products.html
[10]《工業控制系統安全之探討-以西門子S7系列為例》陸冠竹、劉奕賢、劉宗晁、李忠憲。國立成功大學電機工程學系 / 電腦與通信工程研究所。2019 臺灣網際網路研討會線上論文集. URL:https://tanet2019.nsysu.edu.tw/thesises.php
[11]《MITRE ATT&CK MATRIX》MITRE. URL:https://attack.mitre.org/
[12]《SIEMENS SIMATIC NET: S7-CPs for Industrial Ethernet -- CP 343-1 / CP 343-1 EX20》SIEMENS公司. URL:https://cache.industry.siemens.com/dl/files/308/8777308/att_39695/v1/ghb3431_e.pdf
[1]《SIEMENS SIMATIC S7-300: S7-300 Module data - Manual》SIEMENS. URL:https://cache.industry.siemens.com/dl/files/629/8859629/att_55794/v1/s7300_module_data_manual_en-US_en-US.pdf
[2]《SIEMENS SIMATIC S7: S7-1200 Programmable controller - System Manual》SIEMENS. URL:https://cache.industry.siemens.com/dl/files/465/36932465/att_106119/v1/s71200_system_manual_en-US_en-US.pdf
However, not only researchers, but also hackers use the Shodan search engine to find targets. Taking Siemens’ industrial control products as an example [9][10], a search on Shodan with the keyword "Simatic" in July this year showed that there were 2550 ports in the world (including 612 ports in the US, 13 IPv4 ports in Taiwan, 149 ports in Japan, 67 ports in China) that are marked with the names of Siemens industrial products in clear text. Further analysis of the composition of the global data, it includes a total of 372 HoneyPots about hacking behaviors researched by the University of Maryland in the US. After deducting the data of the University, Siemens SNMP service that should only be deployed on the intranet but is actually exposed on the Internet has 1,459 records, Siemens PLC module model S7 has 578 records, and Siemens Modbus that connects SCADA and RTU has 98 records. There are even HTTP ports in the data, which can access the web login page of the PLC module or routing gateway. If the deployer does not change the default account password, or a hacker uses Brute Force to crack the account password, someone may be able to control the PLC module or gateway. In fact, researchers can see some of SIMATIC modules too when searching with Shodan [12], and can directly access them without a password such as viewing intranet information or HMI information.

Shodan.io search query page
![Search query result page: Access to Siemens SIMATIC PLC module without password [12]](https://www.onwardsecurity.com/upload/news_resource_blog_b/ALL_news_resource_blog_22J18_hWjounKCY3.jpg)
Search query result page: Access to Siemens SIMATIC PLC module without password [12]

Exploit-DB: Proof-of-concept programs for Siemens industrial control products
The above is just an example of Siemens industrial control products. More information on other industrial control products, IT products and IoT products can be found on Shodan. The CVE vulnerability items it contains are even more diverse. Besides, the proof-of-concept programs of Exploit-DB are only the tip of the iceberg, because the underground market, hidden on the dark web where hackers trade with each other, is full of attacks and control type malwares.
Deployment errors allow hackers to attack directly
According to the MITRE ATT&CK matrix [11], assuming that Siemens SNMP services and S7 PLC modules exposed to the external network are detected to contain CVE vulnerabilities or other unknown vulnerabilities, they belong to the category of "External Remote Services" on the matrix. They may even be able to perform DoS/DDoS attacks to block services through UDP ports 161, 162 or TCP port 102 exposed on the external network. Blocking services may cause the production line to be unable to monitor or shut down, or even make the production line out of control.
Assuming that the web login page of the PLC module or routing gateway contains vulnerabilities or the account password is stolen, it may be classified as the category of "Exploit Public-Facing Application" on the matrix. If hackers gain complete control, they will be able to use it as a botnet and an attack springboard, or as an Advanced Persistent Threat (APT) for long-term lurking to steal business secrets from the factory.
Assuming that the web login page of the PLC module or routing gateway contains vulnerabilities or the account password is stolen, it may be classified as the category of "Exploit Public-Facing Application" on the matrix. If hackers gain complete control, they will be able to use it as a botnet and an attack springboard, or as an Advanced Persistent Threat (APT) for long-term lurking to steal business secrets from the factory.
Security Deployment: The first line of defense for smart manufacturing management
Next, we will talk about the PDCA cycle of DevSecOps. The so-called security deployment includes Signature Verify, Integrity Checks, Security Configuration, and Security Audit. There are countless details during the process of security setting. The 10 cybersecurity risks of websites listed in OWASP TOP 10 [6] are also applicable to a certain extent for the industrial control environment. According to statistics in 2017, the sixth risk is "Security Misconfiguration".
After the deployment is completed, the next step is the daily maintenance, including monitoring, detecting, analyzing incidents, controlling the scope of the incident, incident response and reporting, and maintaining stable operation. In other words, whether the deployment is good or not will directly affect the security and stability of maintenance and operation.
After the deployment is completed, the next step is the daily maintenance, including monitoring, detecting, analyzing incidents, controlling the scope of the incident, incident response and reporting, and maintaining stable operation. In other words, whether the deployment is good or not will directly affect the security and stability of maintenance and operation.
Defense practices: Correct the deployment errors and redeploy security
In summary, the PDCA cycle disconnection caused by deployment errors includes at least but not limited to the following reasons (in accordance with the PCDA classification), and the suggested solutions are listed after the reasons.
Reason 1: Poor deployment plan (Plan)
- No complete deployment plan before implementation leads to confusion in the implementation architecture
- No separation or weak separation between the internal and external networks due to the lack of deployment plan
- The deployment items that should be included are not included in the deployment checklist because there are so many deployment items and the deployment personnel are careless
- The handover of development vendors or developers is incomplete, without providing the specifications of product security settings for deployers
- The deployment file and user manual created by the development vendors or developers contain incorrect deployment settings
- No post-deployment maintenance monitoring plan leads to no security audit settings
Suggested solutions: Seek help from the professional cybersecurity architect consultant
- Complete deployment plan
- Complete deployment checklist planning
- Complete maintenance and operation monitoring planning
Reason 2: Inadequate capacity and manpower shortage (Do)
- Deployers did not fully understand the industrial control cybersecurity standards
- Deployers only know the hardware installation but do not know that the software and firmware also need to be set
- Deployers are untrained temporary workers
- Deployers are still unfamiliar after training
- Sloppy work on the deployment because of heavy workload, limited time and insufficient manpower
- Deployers do not fully understand about enabling software audits
- Part-time internal auditors only know the handover items of hardware devices
- Deployers did not deploy in accordance with the manual of the industrial control product
Suggested solutions: Seek professional cybersecurity consultant to assist in education and training
- Strengthen the professional cybersecurity education and training for deployers
- Strengthen the professional cybersecurity education and training for auditors
Reason 3: Lack of internal audit during deployment (Check)
- No full-time internal security staff and auditors in the organization
- Unable to check the package before deployment because of poor industrial control product design
- Deployers over rely on automated deployment tools with poor settings
- The deployed industrial control products have been released poorly-developed versions
- Deploy industrial control products that contain vulnerabilities but are not verified and protected
- Deploy industrial control products that lack software audit design and cannot enable audit functions
Suggested solutions
- Set up full-time cybersecurity auditors in accordance with laws and regulations
- Require industrial control product developers to provide product cybersecurity test report tested by a third party laboratory
- Purchase auditable industrial control and monitoring equipment and enable auditing functions
Reason 4: Poor corporate culture (Act)
- Customers or corporate executives lack relevant knowledge of maintenance management and cybersecurity, and neglect the importance of cybersecurity, resulting in no cybersecurity commitment and deployment plan
- During or after deployment, customers or corporate executives request the wrong configurations that facilitate communication between enterprises but lack cybersecurity
- Lack of cybersecurity education and training within the company
- Business owners give maintenance and deployment personnel lower salary, more work hours and excessive workloads, or treat them badly or in an inhumane. Or the essential social value of the products manufactured by the factory is not recognized by employees. All these make employees lack work enthusiasm and job burnout, leading to poor deployment and monitoring quality, and even make employees develop a mentality of revenge and become hackers
Suggested solutions: Seek assistance from professional cybersecurity consultant, corporate management consultant or corporate ethics consultant
- Basic cybersecurity education and training for the entire enterprise
- Improve the overall corporate culture, replace punishment with rewards, and strengthen employees' coherence and execution ability
Onward Security cybersecurity services and self-developed products for smart factory
Onward Security offers cybersecurity services and self-developed products and solutions for smart factory, mainly providing cybersecurity compliance and certification services such as IEC 62443 and ISO 27001. The company is able to assist manufacturers in security deployment plans and audits to quickly obtain international standard certificates, thereby enhancing customer trust and corporate reputation. The cybersecurity testing services of industrial control products or systems can meet the cybersecurity requirements of software and hardware, and are suitable for mobile devices, smart home appliances, smart cars, Netcom, security control and other IoT products, as well as smart manufacturing-related industrial control components such as PLC, ICS, and SCADA.
Meanwhile, the company provides software security development consulting services to assist manufacturers with software security development capabilities, and conducts professional education and training in software development security and maintenance and operation cybersecurity management. Through these, technicians can establish cybersecurity awareness related to the IIoT to respond to the future of smart manufacturing and the advent of the Industry 4.0 era.
"HERCULES SecFlow" is a self-developed product cybersecurity management system that offers a comprehensive systematized solution for product security development and management, and complies with DevSecOps. It provides product security process management, product firmware security detection, proactive product security event monitoring and notification, starting from requirement to design, development, testing and deployment, helping customers quickly establish a secure software development process. It also supports compliance standards such as ISO 27001, ISO 27034, OpenSAMM, NIST SP 800-64. Furthermore, the company continues to develop advanced versions of the next generation to meet the maintenance and operation monitoring requirements before and after deployment. The new versions will offer many advanced functions such as multi-point asset monitoring, risk assessment, and multi-standard cybersecurity policy management, and be suitable for the cybersecurity protection framework - MITRE ATT&CK.
Another product is the Automatic Vulnerability Assessment - "HERCULES SecDevice". It is an automated security assessment tool designed for connected products, and provides several features such as known vulnerability testing, fuzzing testing and web security testing. Due to the use of patented AI learning technology, it speeds up detection and improves the accuracy of vulnerability detection. The scope of testing and evaluation covers security requirements including IEC 62443, OWASP TOP 10 and CWE/SANS TOP 25.
Meanwhile, the company provides software security development consulting services to assist manufacturers with software security development capabilities, and conducts professional education and training in software development security and maintenance and operation cybersecurity management. Through these, technicians can establish cybersecurity awareness related to the IIoT to respond to the future of smart manufacturing and the advent of the Industry 4.0 era.
"HERCULES SecFlow" is a self-developed product cybersecurity management system that offers a comprehensive systematized solution for product security development and management, and complies with DevSecOps. It provides product security process management, product firmware security detection, proactive product security event monitoring and notification, starting from requirement to design, development, testing and deployment, helping customers quickly establish a secure software development process. It also supports compliance standards such as ISO 27001, ISO 27034, OpenSAMM, NIST SP 800-64. Furthermore, the company continues to develop advanced versions of the next generation to meet the maintenance and operation monitoring requirements before and after deployment. The new versions will offer many advanced functions such as multi-point asset monitoring, risk assessment, and multi-standard cybersecurity policy management, and be suitable for the cybersecurity protection framework - MITRE ATT&CK.
Another product is the Automatic Vulnerability Assessment - "HERCULES SecDevice". It is an automated security assessment tool designed for connected products, and provides several features such as known vulnerability testing, fuzzing testing and web security testing. Due to the use of patented AI learning technology, it speeds up detection and improves the accuracy of vulnerability detection. The scope of testing and evaluation covers security requirements including IEC 62443, OWASP TOP 10 and CWE/SANS TOP 25.
References:
[1]《WHITE PAPER : Smarter Security for Manufacturing in The Industry 4.0 Era - Industry 4.0 Cyber Resilience for the Manufacturing of the Future》Broadcom、Symantec. URL:https://docs.broadcom.com/doc/industry-4.0-en
[2]《2019 GLOBAL DATA RISK REPORT FROM THE VARONIS DATA LAB》Varonis。URL:https://info.varonis.com/hubfs/Varonis%202019%20Global%20Data%20Risk%20Report.pdf#page=20
[3]《Recommended Practice: Improving Industrial Control System Cybersecurity with Defense-in-Depth Strategies》Industrial Control Systems Cyber Emergency Response Team, CISA, Department of Homeland Security. URL:https://us-cert.cisa.gov/sites/default/files/recommended_practices/NCCIC_ICS-CERT_Defense_in_Depth_2016_S508C.pdf
[4]《Programmable Logic Controllers - Security Threats and Solutions》Texas Instruments. https://www.ti.com/lit/an/spraco8/spraco8.pdf
[5]《Smart Grid: Security》. URL:https://smartgrid.taipower.com.tw/en/page.aspx?mid=15
[6]《OWASP Top Ten》OWASP. URL:https://owasp.org/www-project-top-ten/
[7]《Shodan Help Center: Navigating the Website》Shodan.io. URL:https://help.shodan.io/the-basics/navigating-the-website
[8]《US government warns over vulnerable control systems》BBC UK. URL:https://www.bbc.com/news/technology-20984827
[9]《CVE Details: Siemens Products》CVE Details. URL:https://www.cvedetails.com/product-list/product_type-/vendor_id-109/firstchar-S/page-3/products.html
[10]《工業控制系統安全之探討-以西門子S7系列為例》陸冠竹、劉奕賢、劉宗晁、李忠憲。國立成功大學電機工程學系 / 電腦與通信工程研究所。2019 臺灣網際網路研討會線上論文集. URL:https://tanet2019.nsysu.edu.tw/thesises.php
[11]《MITRE ATT&CK MATRIX》MITRE. URL:https://attack.mitre.org/
[12]《SIEMENS SIMATIC NET: S7-CPs for Industrial Ethernet -- CP 343-1 / CP 343-1 EX20》SIEMENS公司. URL:https://cache.industry.siemens.com/dl/files/308/8777308/att_39695/v1/ghb3431_e.pdf
[1]《SIEMENS SIMATIC S7-300: S7-300 Module data - Manual》SIEMENS. URL:https://cache.industry.siemens.com/dl/files/629/8859629/att_55794/v1/s7300_module_data_manual_en-US_en-US.pdf
[2]《SIEMENS SIMATIC S7: S7-1200 Programmable controller - System Manual》SIEMENS. URL:https://cache.industry.siemens.com/dl/files/465/36932465/att_106119/v1/s71200_system_manual_en-US_en-US.pdf






