OT Security
21.Dec.2020
Cybersecurity defense practices for smart factory (Part 2)
Neglecting the cybersecurity of industrial control systems can cause significant losses
In the previous article we explored how the cybersecurity protection mechanism would turn into the cybersecurity breach when the smart factory makes errors in the cybersecurity deployment. This article will continue to discuss industrial security risks from another perspective - detection and monitoring mechanisms.
Due to the characteristics of industrial production, there are bound to be risks in the production process. From the input of raw materials and various cutting and grinding that produce physical and chemical changes during the automated process, to the output of products and the disposal of remaining waste, negligence of cybersecurity in any link may affect the manufacturing process and cause significant losses. The possible impacts and losses it may bring include personnel health and safety, environmental protection, output reduction or production line shutdown, product yield reduction, business interruption, financial compensation, administrative penalties by regulatory agencies, sentencing by the judiciary, reputation losses, etc. Additionally, business secrets, intellectual property rights, business contract interruption and compensation that are valued by enterprises are also included.
Due to the characteristics of industrial production, there are bound to be risks in the production process. From the input of raw materials and various cutting and grinding that produce physical and chemical changes during the automated process, to the output of products and the disposal of remaining waste, negligence of cybersecurity in any link may affect the manufacturing process and cause significant losses. The possible impacts and losses it may bring include personnel health and safety, environmental protection, output reduction or production line shutdown, product yield reduction, business interruption, financial compensation, administrative penalties by regulatory agencies, sentencing by the judiciary, reputation losses, etc. Additionally, business secrets, intellectual property rights, business contract interruption and compensation that are valued by enterprises are also included.
Continue Detection & Monitoring: The second line of defense for smart manufacturing management
The impact of lacking detection and monitoring mechanisms
The previous article mentioned that poor deployment of factories will increase the probability of being attacked by hackers. Under this premise, if the factory lacks detection and monitoring mechanisms, the consequences will be more serious. For example, when networked equipment (such as PLC) suffers a denial of service attack that causes the production line to shut down, the factory's front-line workers who lack cybersecurity knowledge are likely to mistake the PLC for aging or crash, and only restart the PLC. If the factory has hired programmers, the supervisor may require them to modify the PLC control program to reduce the number of crashes. However, in the absence of detection and monitoring mechanisms, it is difficult for programmers to understand the truth, and the real cause of the problem also cannot be discovered.
The importance of effective detection and monitoring mechanisms
According to the statistics of OWASP [1] in 2017, it listed the Top 10 Web Application Security Risks and the tenth risk is "Insufficient Logging & Monitoring". Web has universal functional specifications, making it also common in industrial control systems. Therefore, the cybersecurity risk should not be underestimated. As for a large number of industrial control equipments, their communication uses specific specifications or customized protocols, and all have their own unique setting modes. As a result, not only they are difficult to detect vulnerabilities, but also they are impossible to respond to and track security incidents due to their limited data capacity that makes them lack of complete monitoring and log records. Therefore, if the effectiveness of detection and monitoring is insufficient, it will not be able to respond to and deal with the incident immediately when a cybersecurity incident occurs, which may shut down the factory and cause the economic losses or bring the related harm to the enterprise.
Example of attack scenario: How did the hacker invade?
Before the attack: Reconnaissance
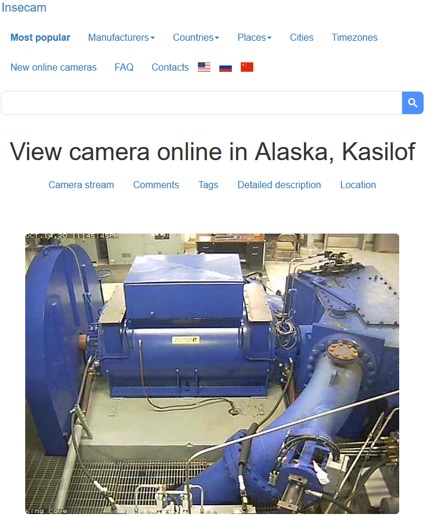
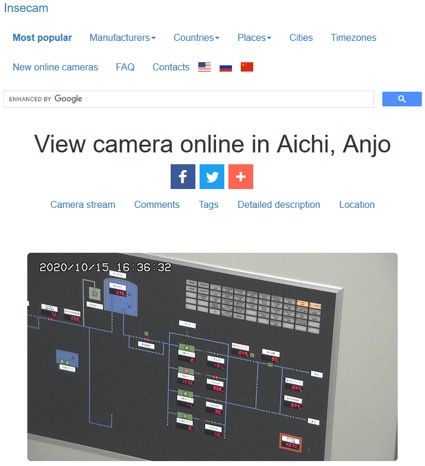
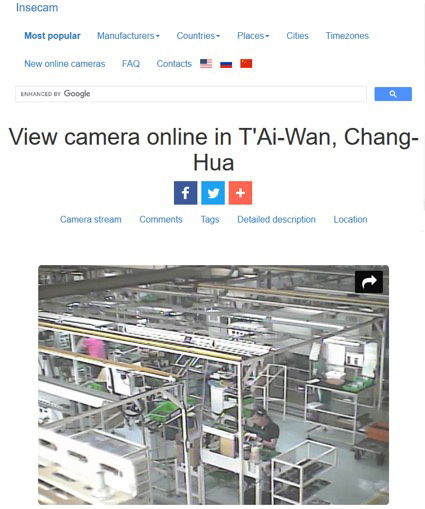
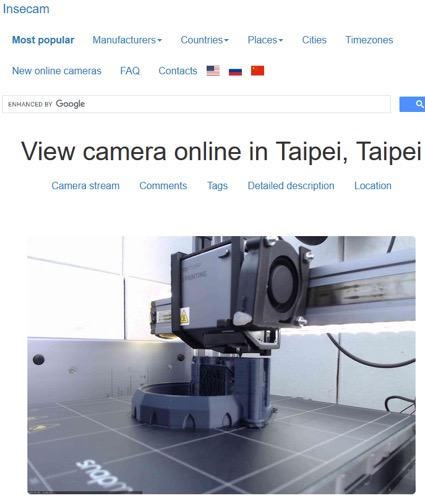
Based on the search technology of Shodan, Google and Russia's Yandex map, the well-known "insecam.org"[2] in the field of cybersecurity collected global CCTV data. The content includes the disclosed geographic location, and the description of the video also includes the IPv4 address and communication protocol port of the disclosed CCTV. Most of them are public surveillance images of traffic and communities. But there are still a lot of videos from private organizations, or home CCTVs and factory operation areas that leak data due to poor deployment. Insecam also includes labels such as industrial and office, and even videos related to eight key infrastructures such as energy and water conservancy.
Through remote reconnaissance, hackers are able to target the factory and be lurking, after getting the geographic location disclosed by insecam.
References:
[1]《OWASP Top Ten》OWASP組織。閱於2020.Oct.15。網址:https://owasp.org/www-project-top-ten/
[2]《Insecam》Insecam組織。閱於2020.Jul.09~Oct.15。網址:https://www.insecam.org/en/
[3]《惡名昭彰的殭屍網路病毒Mirai作者之一被判賠償860萬美元》台灣iThome。閱於2020.Oct.16。網址:https://www.ithome.com.tw/news/126699
[4]《BASHLITE Malware Uses IoT for DDoS Attacks》Security Intelligence。閱於2020.Oct.16。網址:https://securityintelligence.com/news/bashlite-malware-uses-iot-for-ddos-attacks/
[5]《This new variant of Mirai botnet malware is targeting network-attached storage devices》ZDNet。閱於2020.Oct.16。網址:https://www.zdnet.com/article/this-new-variant-of-mirai-botnet-malware-is-targeting-network-attached-storage-devices/
[6]《Grandstream and DrayTek Devices Exploited to Power New Hoaxcalls DDoS Botnet》Palo Alto Networks之IoC報告。閱於2020.Oct.16。網址:https://unit42.paloaltonetworks.com/new-hoaxcalls-ddos-botnet/
[7]《什麼是 APT進階持續性威脅 (Advanced Persistent Threat, APT)?》Trend Micro。閱於2020.Oct.16。網址:https://blog.trendmicro.com.tw/?p=123
[8]《Most ICS vulnerabilities disclosed this year can be exploited remotely》Help Net Security。閱於2020.Oct.16。網址:https://www.helpnetsecurity.com/2020/08/20/ics-vulnerabilities-exploited-remotely/
[9]《MITRE ATT&CK MATRIX》MITRE組織。閱於2020.Jul.08。網址:https://attack.mitre.org/
[10]《Building Trojan Hardware at Home》BlackHat 2014。閱於2020.Jul.09。網址:https://www.blackhat.com/docs/asia-14/materials/Dunning/Asia-14-Dunning-Building-Trojan-Hardware-At-Home.pdf
[11]《The 'killer USB' that FRIES laptops: Malicious drive uses a high voltage to destroy the computer's circuit board》Daily Mail。閱於2020.Oct.15。網址:https://www.dailymail.co.uk/sciencetech/article-2997401/The-killer-USB-FRIES-laptops-Malicious-drive-uses-high-voltage-destroy-computer-s-circuit-board.html
[12]《Knowing Your Employees - An Overview》Management Study Guide。閱於2020.Oct.16。網址:https://www.managementstudyguide.com/knowing-your-employees.htm
[13]《世界備份日( World Backup Day):三二一原則》Trend Micro。閱於2020.Oct.16。網址:https://blog.trendmicro.com.tw/?p=4707
[14]《What is Cyber Hygiene? A Definition of Cyber Hygiene, Benefits, Best Practices, and More》Digital Guardian。閱於2020.Oct.16。網址:https://digitalguardian.com/blog/what-cyber-hygiene-definition-cyber-hygiene-benefits-best-practices-and-more
 |
 |
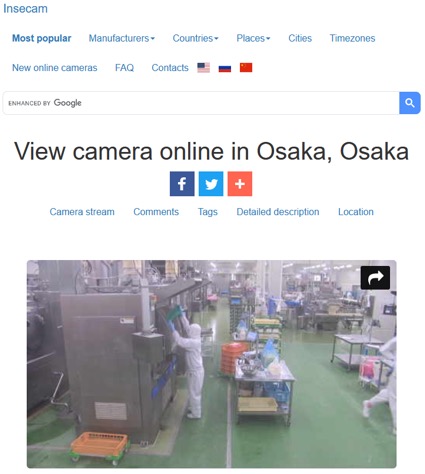 |
| The leaked video about the hydroelectric power plant in Alaska, U.S. | The leaked video about the hydraulic facilities in Aichi, Japan | The leaked video about the internal operation of a food processing factory in Osaka, Japan |
 |
 |
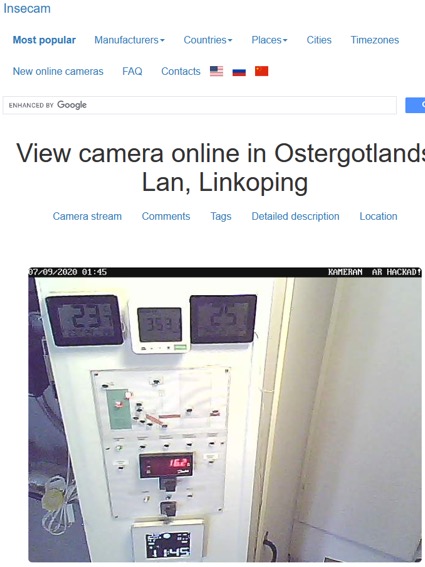 |
| The leaked video about a factory in Changhua, Taiwan | The leaked video of a private device undergoing 3D printing(located in an alley on Songjiang Road near the north of Guanghua Digital Plaza in Taipei) | CCTV somewhere in Sweden has been hacked (Jul.09.2020) |
Through remote reconnaissance, hackers are able to target the factory and be lurking, after getting the geographic location disclosed by insecam.
Attack method 1: Exploit the known vulnerabilities of the device to invade the target through a remote connection
In 2016, the infamous malware "Mirai"[3] infected many CCTVs and other devices on the Internet, and many IoT devices were infected by the malware "BASHLITE"[4]. The reason for the infection is that the BusyBox package with vulnerabilities was used in software development, and the software cannot be updated. Both well-known malwares infect the devices and use them as botnets to carry out multiple Distributed Denial of Service (DDoS) attacks that cause serious losses to enterprises. There are still many modified variants [5] [6] that continue to attack and infect on the Internet. In addition to DDoS, the ransomware infestation and the so-called Advanced Persistent Threat (APT) [7] are also common at present. According to statistics, 70% of the known vulnerabilities of industrial control systems (ICS) can be exploited remotely. Among them, the rate of exploiting the vulnerability of remote code execution to hack the industrial control systems accounted for 49%, and the rate of performing DoS attacks after hacking can be as high as 39% too. [8]Attack method 2: Physical intrusion through supply chain penetration leads to supply chain compromise
According to the "Supply Chain Compromise" mentioned in the MITRE ATT&CK matrix, hacking techniques in the industrial control field may include using software update mechanisms to replace software, intercepting components or equipments to implant malicious programs, pretending to be upstream/downstream suppliers or third-party vendors to sell problematic components, and so on. Meanwhile, it is also possible that, like the previous ransomware incident of a well-known semiconductor manufacturing company, a third-party manufacturer inadvertently brought in equipment with malicious software, causing damage to the equipment in the factory. The economic model of modern manufacturing requires cooperation with upstream manufacturers, third-party vendors, and downstream manufacturers. Therefore, it is necessary to pay attention to and strengthen the management of cybersecurity.Attack method 3: Exploit asset equipment without identification mechanism to carry out physical intrusion
The MITRE ATT&CK matrix [9] also mentions "Hardware Additions", which means that hackers may enter the factory with malicious hardware. The addition of unchecked and unauthorized hardware can lead to changes in hardware functionality, information leakage, reduction of hardware credibility, and denial of service. The techniques include bringing in mini camera, external disk drive containing malicious program, miniature wireless signal collectors and transmitters, or inserting a message recorder at one end of the network cable to record illegally, as well as using USB or Ethernet cable that contains high-voltage capacitors to damage the equipment and interrupt production, etc. How to avoid this kind of physical intrusion caused by the addition or removal of software and hardware? Strengthening asset inventory and identification, and monitoring data flow will be important issues in the future. |
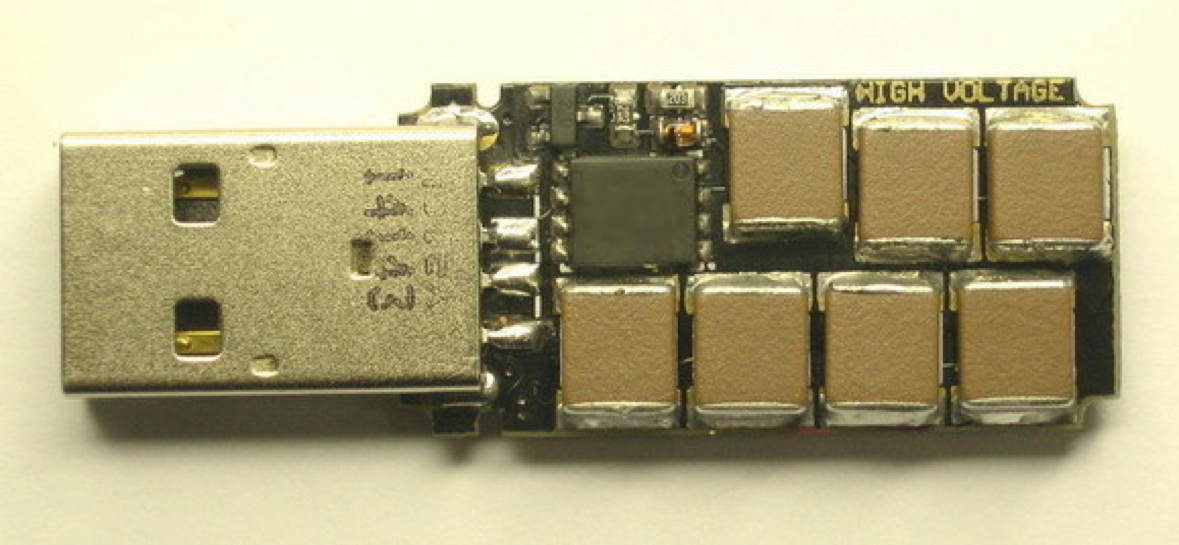 |
| At the international security conference - Black Hat Asia 2014, the speaker showed the mouse with malicious hardware added [10] | In 2015, Russian hackers developed a USB Killer, which can release high voltage when connected to the device, to destroy the hardware without voltage protection [11] |
Defense practice: Security Management
1. Plan - Establish a security management plan
- The executives of the enterprise make a security commitment and initiate security management.
- Establish a compliant maintenance and operation monitoring plan - the following are the reference standards: IEC-62443 series, IEC-61511 series, IEC/ISO-27000 series, IES/ISO-27036, NIST SP 800-82, NIST SP 800-39 and other series of cybersecurity standards.
- Establish cybersecurity management procedures and checklists based on the implemented standards, including risk assessment and other processes.
- The purchased hardware equipment and software must have necessary and effective cybersecurity monitoring and security process management, or select software and hardware that have been certified by third-party organizations, such as products that have passed ISO/IEC 15408: Common Criteria.
- Enhance the understanding of employees (KYE: Know Your Employees) [19].
- For the possibility of the worst case, there must be a plan to deal with it.
- Take out cybersecurity insurance to deal with economic losses caused by cybersecurity incidents because even the best-laid plans can sometimes go awry.
2. Do - Implement security management program
- Inventory and classify various software and hardware assets.
- Implement cybersecurity requirements in accordance with the various control measures of the implemented cybersecurity standards.
- Regularly carry out data backup according to the "3-2-1 backup principle"[13], and reserve spare hardware equipment to prevent natural disasters, human negligence, and malicious software damage.
- Conduct "Cyber Hygiene" [14] on assets, assuming that they have been hacked.
- Adjust the security principles of the operating system to meet the requirements of the implemented cybersecurity standards.
- Set the Allowed List for intranet and enable IPsec or MACsec settings if necessary.
- Strengthen internal network security detection and continue to maintain "Cyber hygiene".
- Record and analyze the data flow between each access point.
- Adopt "Zero Trust" for cybersecurity incidents when they occur.
- Allocate sufficient manpower to monitor software logs.
- Maintain the hardware equipment regularly.
- Require software security updates from a trusted source, and even require code signing certificate.
3. Check - Regular internal and external audits
- Enhance the education and training of internal cybersecurity management and audit personnel.
- Periodically evaluate the useful life of assets.
- Regularly check the hardware equipment and software logs.
- Audit one by one according to the checklist established by the implemented cybersecurity standards.
- Document the audit results.
- Report cybersecurity incidents and response measures in accordance with laws and regulations.
4. Act. - Review and improve security deficiencies and revise security management plans
- Compare unresolved security deficiencies and tolerable security deficiencies in accordance with cybersecurity incidents and standards.
- Identify and evaluate existing response measures.
- Reassess the possibility and impact of the recurrence of cybersecurity incidents.
- Identify additional cybersecurity response measures.
- Add additional response measures to the security management plan.
Smart factory cybersecurity solutions provided by Onward Security
Onward Security offers a variety of smart factory cybersecurity solutions, including ISO 27001 and IEC 62443 compliance consulting services, cybersecurity testing services for industrial control products or system software and hardware (such as PLC, ICS, SCADA and other smart manufacturing related industrial control components), and self-developed automation platform - HERCULES for product cybersecurity compliance management. These solutions can scan and manage common cybersecurity vulnerabilities in smart manufacturing factories. In addition, Onward Security provides software security development consulting services to assist vendors in possessing the capacities of software security development. We also provide vendors with professional software development security training and maintenance and operation cybersecurity management training, helping technicians establish cybersecurity awareness related to the Industrial Internet of Things (IIoT), in order to respond to the future of smart manufacturing and the advent of the Industry 4.0 era.References:
[1]《OWASP Top Ten》OWASP組織。閱於2020.Oct.15。網址:https://owasp.org/www-project-top-ten/
[2]《Insecam》Insecam組織。閱於2020.Jul.09~Oct.15。網址:https://www.insecam.org/en/
[3]《惡名昭彰的殭屍網路病毒Mirai作者之一被判賠償860萬美元》台灣iThome。閱於2020.Oct.16。網址:https://www.ithome.com.tw/news/126699
[4]《BASHLITE Malware Uses IoT for DDoS Attacks》Security Intelligence。閱於2020.Oct.16。網址:https://securityintelligence.com/news/bashlite-malware-uses-iot-for-ddos-attacks/
[5]《This new variant of Mirai botnet malware is targeting network-attached storage devices》ZDNet。閱於2020.Oct.16。網址:https://www.zdnet.com/article/this-new-variant-of-mirai-botnet-malware-is-targeting-network-attached-storage-devices/
[6]《Grandstream and DrayTek Devices Exploited to Power New Hoaxcalls DDoS Botnet》Palo Alto Networks之IoC報告。閱於2020.Oct.16。網址:https://unit42.paloaltonetworks.com/new-hoaxcalls-ddos-botnet/
[7]《什麼是 APT進階持續性威脅 (Advanced Persistent Threat, APT)?》Trend Micro。閱於2020.Oct.16。網址:https://blog.trendmicro.com.tw/?p=123
[8]《Most ICS vulnerabilities disclosed this year can be exploited remotely》Help Net Security。閱於2020.Oct.16。網址:https://www.helpnetsecurity.com/2020/08/20/ics-vulnerabilities-exploited-remotely/
[9]《MITRE ATT&CK MATRIX》MITRE組織。閱於2020.Jul.08。網址:https://attack.mitre.org/
[10]《Building Trojan Hardware at Home》BlackHat 2014。閱於2020.Jul.09。網址:https://www.blackhat.com/docs/asia-14/materials/Dunning/Asia-14-Dunning-Building-Trojan-Hardware-At-Home.pdf
[11]《The 'killer USB' that FRIES laptops: Malicious drive uses a high voltage to destroy the computer's circuit board》Daily Mail。閱於2020.Oct.15。網址:https://www.dailymail.co.uk/sciencetech/article-2997401/The-killer-USB-FRIES-laptops-Malicious-drive-uses-high-voltage-destroy-computer-s-circuit-board.html
[12]《Knowing Your Employees - An Overview》Management Study Guide。閱於2020.Oct.16。網址:https://www.managementstudyguide.com/knowing-your-employees.htm
[13]《世界備份日( World Backup Day):三二一原則》Trend Micro。閱於2020.Oct.16。網址:https://blog.trendmicro.com.tw/?p=4707
[14]《What is Cyber Hygiene? A Definition of Cyber Hygiene, Benefits, Best Practices, and More》Digital Guardian。閱於2020.Oct.16。網址:https://digitalguardian.com/blog/what-cyber-hygiene-definition-cyber-hygiene-benefits-best-practices-and-more






