OT Security
12.Oct.2020
Industrial control security standard and practice - A brief overview of the IEC62443
On December 23, 2015, the Ukrainian power grid was attacked by a hacker, resulting in a blackout in the Ivano-Frankivsk region. This is the world’s first large-scale power outage caused by a hacker attack, and has caused all parties to attach great importance to the cybersecurity threats of critical infrastructure. In Taiwan, the cybersecurity incidents in the manufacturing, industrial and medical industries have successively occurred since the machines infected with viruses in the semiconductor industry in 2018. These are only part of large-scale and complex attacks. The above-mentioned cybercriminals attacking important infrastructure systems have led many cybersecurity vendors to invest in research on the cybersecurity risks and response strategies of major livelihood infrastructure. The OT cybersecurity is getting more and more attention as well. Therefore, the International Electrotechnical Committee (IEC) has successively released a series of IEC 62443 standards since 2013. Taiwan, which started out in manufacturing, is of course also required by major European and American customers to obtain a certificate in compliance with the IEC 62443 series of industrial control standards to reduce the cybersecurity risk of industrial control.
How much do you know about the security of industrial control IoT?
In response to the development of the Internet of Things (IoT), industrial control systems include more and more automated control systems, computer computing and server services. The popularity and integration of Internet has threatened the security of OT systems. The fact coupled with the recent increase in political conflicts, terrorism and economic crimes are all motives for attacking the critical infrastructure of the industry. For this reason, the IEC specifically made IEC 62443 with reference to ISA 99 standard for industrial control security. After that, the ISA 99 was renamed ISA/IEC 62443. ISA/IEC 62443 has different series of standards, allowing upstream, midstream and downstream manufacturers in each industrial control field to have their own corresponding standards, without the need to apply to all manufacturers. This approach enables manufacturers to reduce the cost and manpower of introducing cybersecurity standards. Meanwhile, it can quickly find out the cause and take appropriate measures when a cybersecurity incident occurs.
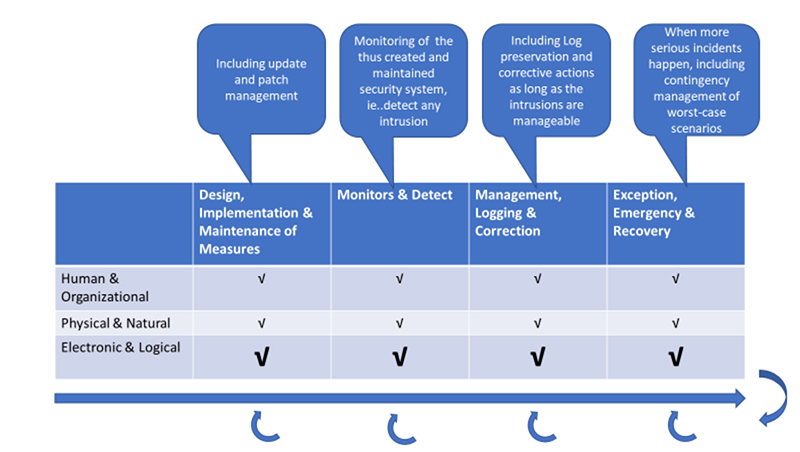
Figure 1: IEC/PAS 62443-3 Security life cycle
The cybersecurity life cycle of a product can be viewed from three perspectives: human-machine interface, physical environment and electronic logic interface. From design, deployment, operation, monitoring, management, emergency handling and maintenance, each stage is interlocked with one another. The IEC/PAS 62443-3 standard pays more attention to the life cycle of industrial control security. It can be seen from Figure 1 that there are corresponding matters to be paid attention to at each stage. The purpose is to reduce security risks and threats to maintain cybersecurity throughout the product life cycle.
The common threats of industrial control systems can come from public saboteurs or terrorists. After being attacked, the failure of the industrial control system may cause cybersecurity incidents, block attacks, confidentiality vulnerabilities (such as the disclosure of production information), legal loopholes, or natural disasters (such as unexpected natural disasters). As each organization has its own special considerations, the reporting management level, reporting speed, related response measures, and involved supervisor level are all determined in accordance with the severity of the impact on product functions. In order to avoid the occurrence of these threats, risk assessment is an indispensable part of the activities of industrial control security. Measures to reduce risks can be implemented by means of money investment, technology use, physical protection design, and organization management, so as to jointly protect the value of assets.
The aspects to be considered in industrial control security must be extensive. Therefore, the standard of IEC 62443 reference various standards, including the ISO/IEC 15408 common criteria (physical security, product development life cycle, etc.), ISO/IEC 27002 best practices for cybersecurity, ISO/IEC 27001 cybersecurity management system, ISO/IEC Guide 73:2002 risk assessment, NIST 800-53 risk control measures, and ISO 19790 cryptographic modules. It is the hope that the industrial control security regulations can be formulated from a variety of different angles and different exposure levels.
Different from the general ISO/IEC standard, if you want to obtain the certificate of IEC 62443-4-2 or IEC 62443-3-3, you must first pass the certification of IEC 62443-4-1. In other words, for product suppliers, they must first ensure the security of the product development process within the organization before applying for product security certification. Currently, IoT devices exported to foreign markets are increasingly required to provide equipment Security Level certification. The IEC 62443-4-2 regulates many details related to Security Level. As the market's demand for security increases, IEC62443-4-2 certification is becoming increasingly important.
Regarding the verification of IEC 62443-4-2, there are four types of components: Software Application, Embedded Device, Network Device and Host Device. The components of IEC 62443-4-2 must be implemented according to the development process defined by IEC 62443-4-1. Furthermore, the technical security needs to meet all the requirements of the customized Security Level. After completion, the certificate can be obtained.
However, for organizations with development capabilities, they already have an existing product development process. How can they be adjusted to meet the requirements of IEC 62443-4-1 for product security development?
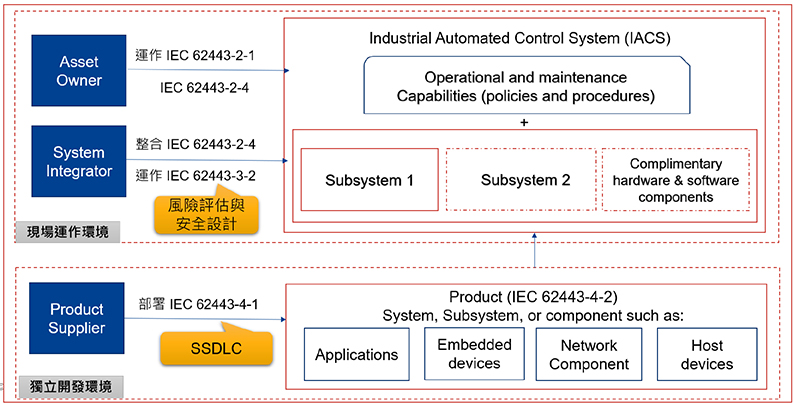
Figure 2: Corresponding diagram of roles and standard processes
From the corresponding relationship between each role and the standard process (see Figure 2: Corresponding diagram of roles and standard processes), it can be concluded that there are two implementation priorities for the development environment. The first is the framework of security development. It includes security design, concept of defense in depth, and how to manage the product life cycle (including the process of establishment, maintenance and product failure). The second is that during the development process the details of product development (including security configuration, update management policies, and other related security development processes) must be properly recorded and retained. Meanwhile, the security testing must be performed to meet the requirements of the IEC 62443-4-1 security development process.

Figure 3: Maturity Level and Security Level
References:
[1] IEC/PAS 62443-3 Publicly available specification Pre-Standard
[2] IEC/PAS 62443-4-1 Secure Product Development Lifecycle Requirements
The life cycle and threat of industrial control products!
The essence of cybersecurity is regarded as a life cycle that never stops, unless the product is declared as an end of license. During the product life cycle, it is necessary to continuously and regularly take security measures for the industrial control system (ICS) to prevent multi-faceted cybersecurity threats.
Figure 1: IEC/PAS 62443-3 Security life cycle
The cybersecurity life cycle of a product can be viewed from three perspectives: human-machine interface, physical environment and electronic logic interface. From design, deployment, operation, monitoring, management, emergency handling and maintenance, each stage is interlocked with one another. The IEC/PAS 62443-3 standard pays more attention to the life cycle of industrial control security. It can be seen from Figure 1 that there are corresponding matters to be paid attention to at each stage. The purpose is to reduce security risks and threats to maintain cybersecurity throughout the product life cycle.
The common threats of industrial control systems can come from public saboteurs or terrorists. After being attacked, the failure of the industrial control system may cause cybersecurity incidents, block attacks, confidentiality vulnerabilities (such as the disclosure of production information), legal loopholes, or natural disasters (such as unexpected natural disasters). As each organization has its own special considerations, the reporting management level, reporting speed, related response measures, and involved supervisor level are all determined in accordance with the severity of the impact on product functions. In order to avoid the occurrence of these threats, risk assessment is an indispensable part of the activities of industrial control security. Measures to reduce risks can be implemented by means of money investment, technology use, physical protection design, and organization management, so as to jointly protect the value of assets.
The aspects to be considered in industrial control security must be extensive. Therefore, the standard of IEC 62443 reference various standards, including the ISO/IEC 15408 common criteria (physical security, product development life cycle, etc.), ISO/IEC 27002 best practices for cybersecurity, ISO/IEC 27001 cybersecurity management system, ISO/IEC Guide 73:2002 risk assessment, NIST 800-53 risk control measures, and ISO 19790 cryptographic modules. It is the hope that the industrial control security regulations can be formulated from a variety of different angles and different exposure levels.
How much do you know about IEC 62443 certification!
The certification standards provided by IEC62443 include two categories of program flow and product security, as shown in the following table:| Certification category | Standard | Applicable vendor |
|---|---|---|
| Procedure flow | 62443-2-4 Security program requirements for IACS service providers | System integrator |
| 62443-4-1 Secure product development lifecycle requirements | Product supplier | |
| Product Security | 62443-3-3 System Security requirements and security levels | System integrator |
| 62443-4-2 Technical Security requirements for IACS components | Product supplier |
Table 1: Certification categories and system standards
Different from the general ISO/IEC standard, if you want to obtain the certificate of IEC 62443-4-2 or IEC 62443-3-3, you must first pass the certification of IEC 62443-4-1. In other words, for product suppliers, they must first ensure the security of the product development process within the organization before applying for product security certification. Currently, IoT devices exported to foreign markets are increasingly required to provide equipment Security Level certification. The IEC 62443-4-2 regulates many details related to Security Level. As the market's demand for security increases, IEC62443-4-2 certification is becoming increasingly important.
Regarding the verification of IEC 62443-4-2, there are four types of components: Software Application, Embedded Device, Network Device and Host Device. The components of IEC 62443-4-2 must be implemented according to the development process defined by IEC 62443-4-1. Furthermore, the technical security needs to meet all the requirements of the customized Security Level. After completion, the certificate can be obtained.
However, for organizations with development capabilities, they already have an existing product development process. How can they be adjusted to meet the requirements of IEC 62443-4-1 for product security development?
The most important basis for certification - product security development process

Figure 2: Corresponding diagram of roles and standard processes
From the corresponding relationship between each role and the standard process (see Figure 2: Corresponding diagram of roles and standard processes), it can be concluded that there are two implementation priorities for the development environment. The first is the framework of security development. It includes security design, concept of defense in depth, and how to manage the product life cycle (including the process of establishment, maintenance and product failure). The second is that during the development process the details of product development (including security configuration, update management policies, and other related security development processes) must be properly recorded and retained. Meanwhile, the security testing must be performed to meet the requirements of the IEC 62443-4-1 security development process.
Product security strength - Maturity Level and Security Level

Figure 3: Maturity Level and Security Level
The degree of product security required by each organization is different. As a result, IEC62443 not only defines the processes that different roles should follow, but also defines the process maturity level and product security level (see Figure 3: Maturity Level and Safety Level). This allows organizations that want to obtain certification to have a clearer reference.
The Maturity Level of IEC62443 can be used as a reference for the organization to assess the level of the existing internal development process. It is helpful to them in selecting the appropriate Maturity Level as the objective, and provides a clear direction for organizations that want to obtain IEC62443-4-1 certification.
In addition to the Maturity Level, IEC62443 emphasizes the concept of product security assurance. It divides the product Security Level into four levels for product security standards. Each level has different requirements and the types of attacks to be solved also have different requirements. Organizations that want to obtain IEC62443-4-2 certification must first set the Security level objectives they want to achieve for their products. Only in this way can there be an implementation direction to follow.
The Maturity Level of IEC62443 can be used as a reference for the organization to assess the level of the existing internal development process. It is helpful to them in selecting the appropriate Maturity Level as the objective, and provides a clear direction for organizations that want to obtain IEC62443-4-1 certification.
In addition to the Maturity Level, IEC62443 emphasizes the concept of product security assurance. It divides the product Security Level into four levels for product security standards. Each level has different requirements and the types of attacks to be solved also have different requirements. Organizations that want to obtain IEC62443-4-2 certification must first set the Security level objectives they want to achieve for their products. Only in this way can there be an implementation direction to follow.
Industrial control cybersecurity solution for IIoT
Onward Security has successfully assisted dozens of vendors to implement security measures, including the Information Security Management System (ISMS), Secure Software Development Life Cycle (SSDLC), EU’s General Data Protection Regulation (GDPR), the cybersecurity requirements of US Food and Drug Administration (FDA), the common standards ISO 15408, IEC 62443, etc. Especially for the IEC 62443-4-1 standard that was announced in 2018, Onward Security has assisted many vendors to complete the implementation of the 4-1 standard and obtain the IEC 62443-4-1 certificate.
Besides, during the implementation, we found that IIoT device developers have common problems in the development security process, including not controlling the software/firmware security development process or requirements, using package management with known vulnerabilities, and not establishing security incident response and tracking mechanism, etc. Onward Security is capable of giving the right help for the common problems of enterprise product development life cycle management and tailoring the appropriate cybersecurity management process. In the meantime, we provide networking equipment security solutions "HERCULES - Automated Product Security Assessment Platform" to assist in meeting compliance requirements. Its "HERCULES SecFlow - Product Security Management System" allows the R&D team to confirm whether there are major cybersecurity vulnerabilities in the system through using Open Source Risk Management during the software design and development stage, thereby protecting and correcting from the source. By tying in with the "HERCULES SecDevice - Automated Vulnerability Assessment Tool" to provide networking product testing environment configuration, security assessments and other automated functions, the team can discover known and unknown vulnerabilities in more than 120 test items. This allows the team to perform dual security checks during the design and testing phases, effectively reducing cybersecurity risks for products before they go to market.
Besides, during the implementation, we found that IIoT device developers have common problems in the development security process, including not controlling the software/firmware security development process or requirements, using package management with known vulnerabilities, and not establishing security incident response and tracking mechanism, etc. Onward Security is capable of giving the right help for the common problems of enterprise product development life cycle management and tailoring the appropriate cybersecurity management process. In the meantime, we provide networking equipment security solutions "HERCULES - Automated Product Security Assessment Platform" to assist in meeting compliance requirements. Its "HERCULES SecFlow - Product Security Management System" allows the R&D team to confirm whether there are major cybersecurity vulnerabilities in the system through using Open Source Risk Management during the software design and development stage, thereby protecting and correcting from the source. By tying in with the "HERCULES SecDevice - Automated Vulnerability Assessment Tool" to provide networking product testing environment configuration, security assessments and other automated functions, the team can discover known and unknown vulnerabilities in more than 120 test items. This allows the team to perform dual security checks during the design and testing phases, effectively reducing cybersecurity risks for products before they go to market.
References:
[1] IEC/PAS 62443-3 Publicly available specification Pre-Standard
[2] IEC/PAS 62443-4-1 Secure Product Development Lifecycle Requirements






