Blog
DEKRA launches the first Pilot Program for the Delegated Act of RED Directive
As the world becomes increasingly connected, Cyber Security is becoming more and more important. In order to ensure a safe and secure online environment, the European Commission has established a number of new regulations for Cyber Security as the NIS2 Directive, the Cyber Resilience Act, the Digital Operational Resilience Act, and the RED Delegated Act. Since security is firmly anchored in our DNA, DEKRA is actively participating in the development of these regulations.
From Penetration Testing to Red Team Assessment, the Diagnosis of Potential Information Security Threats is Expanded
More companies tend to adopt penetration testing. Through annual penetration testing, they plan to identify potential security vulnerabilities in key systems and fix them accordingly.
ioXt intelligence: A Q&A with Morgan Hung, general manager of Onward Security
From cybersecurity certifying top global manufacturers and brands like TikTok to partnering with government agencies like National Institute of Standards and Technology (NIST), ioXt Alliance is fortunate to collaborate with leaders and influencers involved in the IoT industry. And, we want to bring you their thoughts on the topics that matter most.
Vulnerabilities are impacting millions of smart and industrial IoT devices
The multi-billion-dollar Internet of Things (IoT) market has manufacturers pining for a competitive edge and their risky shortcuts to lead the race have security leaders on high alert.
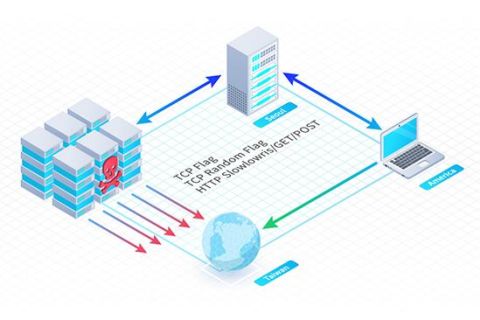
Challenges and solutions of global equipment manufacturers on DoS attacks
The diversified development of the Internet of Things (IoT) has brought business opportunities to various sectors. Many industries have successively launched connected products. In addition to the smart home appliance, smart camera and other consumer products, the non-consumer equipments in industrial control, medical, communications, transportation and other industries have also joined the ranks of the IoT. However, for this booming business opportunity, no one is happiest than the black industry chain. The fields that were originally difficult to capture have created new blueprints for attacks because of devices connected to the Internet. Instantly, devices newly added to the connected world become targets for hackers to access.
The stay-at-home economy thrives during the pandemic, how to stop hackers and protect online transactions
Starting from February 2020, the COVID-19 pandemic has created a whirlwind of stay-at-home economy in the market. The usage rate of e-commerce platforms and video streaming platforms has increased significantly. However, many information security issues are hidden in online trading websites or platforms. As early as 2016, a security researcher had notified Uber of a security vulnerability that could allow attackers to brute force guessing to obtain Uber coupon codes with limited usage and value in the US dollar between $5,000 to $25,000[6].