Blog
DDoS attack re-evolution: TCP Middlebox Reflection can amplify packets by 65-fold
Researchers have observed multiple Distributed Denial-of-Service (DDoS) attacks in recent weeks. These attacks include high-traffic attacks such as SYN flood, and have caused high amounts of traffic that peaked at 11 Gbps. After analyzing the packets used in these DDoS attacks, researchers discovered that the hackers were using a new technique called TCP Middlebox Reflection. It is a very new attack method, first disclosed in a paper by researchers at the University of Maryland and the University of Colorado Boulder in August 2021.
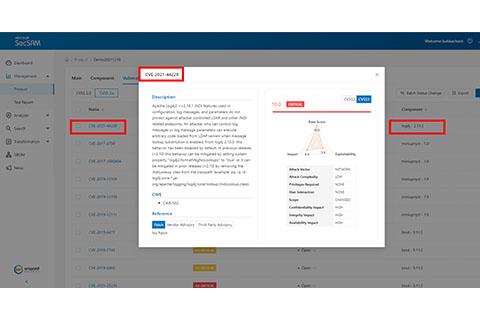
Avoid falling victim to the worst zero-day vulnerability in recent years! Understanding what Apache log4j is? How to patch the CVE-2021-44228 vulnerability
The Apache Foundation issued a serious vulnerability warning about log4j earlier. Log4j is a common open-source logging framework. Many developers use it to log activity in their applications. The reported remote code execution vulnerability (CVE-2021-44228) exists in all versions of log4j 2.x to 2.16.0 (released 2021/12/13). This vulnerability is called "Log4Shell".
Software vulnerabilities become hacker targets again - How to address supply chain security risks?
The source of this risk affecting dozens of brands and millions of devices is a path traversal vulnerability. The Path Traversal vulnerability allows hackers to bypass authentication and browse numerous directories on the victim host. Once hacked, hackers can gain control of the victim host, and even gain superuser (also called root) privileges. Because of this, the CVSS v3 score for the CVE-2021-20090 vulnerability is as high as 9.8.
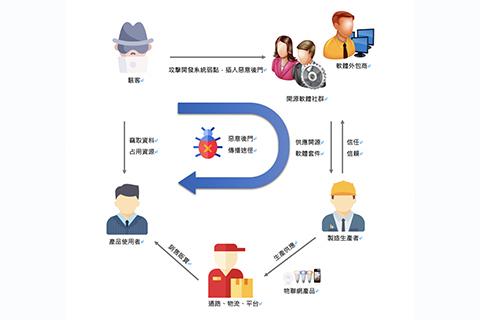
Hackers using open-source software to attack supply chains nowadays, open-source software becomes the scapegoat
Hackers are continuously growing their cyberattack methods in various ways. The Advanced Persistent Threat (APT) is moving their target from enterprises’ cybersecurity to the supply chain. The cybersecurity team constantly ignores open-source software security issues. Therefore, it wins hackers' favor.